
Επικαιροποιημένο: 27 Σεπτεμβρίου 2024
Δεν έχετε χρόνο για χάσιμο; Αυτή είναι η καλύτερη υπηρεσία VPN για τους περισσότερους χρήστες:
- 🥇 ExpressVPN (No\#1 το 2024) — Διαθέτει εξαιρετική ασφάλεια, απίστευτα γρήγορες ταχύτητες και εύχρηστες εφαρμογές για κάθε συσκευή και λειτουργικό σύστημα. Το ExpressVPN διατηρεί μια αυστηρή πολιτική μη καταγραφής, προσφέρει την καλύτερη εμπειρία streaming, torrenting και gaming, ενώ προστατεύει κάθε αγορά με εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών χωρίς κανέναν κίνδυνο.
Κάθε VPN ισχυρίζεται πως είναι το καλύτερο της αγοράς, ωστόσο, αυτό σπάνια ισχύει. Από την εμπειρία μου, πολλά εξ αυτών στερούνται βασικών λειτουργιών ασφαλείας, δεν λειτουργούν με δημοφιλείς ιστότοπους streaming, διαθέτουν κακή υποστήριξη P2P (κοινή χρήση αρχείων), είναι πολύ αργά και προσφέρουν δύσχρηστες ή ελλαττωματικές εφαρμογές.
Πραγματικά, ήθελα να βρω τις καλύτερες εταιρείες, για τον λόγο αυτό δοκίμασα 80+ παρόχους VPN. Εξέτασα τις λειτουργίες ασφαλείας και απορρήτου, τις ταχύτητες, την υποστήριξη streaming και torrenting, το μέγεθος των δικτύων διακομιστών τους και την ικανότητά τους για πρόσβαση στο διαδίκτυο από περιοχές που υπόκεινται σε περιορισμούς. Επίσης, έλεγξα τα VPN των εν λόγω παρόχων ως προς τις δυνατότητές τους στον τομέα του gaming, την παροχή φιλικών προς τον χρήστη εφαρμογών για κάθε κορυφαίο λειτουργικό σύστημα καθώς και ως προς το κόστος τους.
Έπειτα, σύγκρινα και ταξινόμησα τα 10 καλύτερα VPN σύμφωνα με τη συνολική αξία που προσφέρουν. Η Νο#1 επιλογή μου είναι το ExpressVPN, επειδή πληροί όλες τις προϋποθέσεις — είναι το γρηγορότερο VPN εκεί έξω, διαθέτει εξαιρετικές λειτουργίες ασφαλείας και απορρήτου, προσφέρει κορυφαία υποστήριξη streaming και torrenting, ενώ συνοδεύεται από εξαιρετικά εύχρηστες εφαρμογές. Επισήμανση συντακτών: Το ExpressVPN και ο εν λόγω ιστότοπος βρίσκονται υπό κοινή ιδιοκτησία.
ΔΟΚΙΜΑΣΤΕ ΤΟ EXPRESSVPN (30 ΗΜΕΡΕΣ ΧΩΡΙΣ ΚΑΝΕΝΑ ΡΙΣΚΟ)
Σύνοψη της λίστας με τις καλύτερες υπηρεσίες VPN το 2024:
- 1.🥇 ExpressVPN το καλύτερο VPN συνολικά το 2024 — Κορυφαία ασφάλεια και λειτουργίες, οι πιο υψηλές ταχύτητες.
- 2.🥈 PIA VPN το πιο ευέλικτο VPN — Ασφαλές, καλό για streaming και torrenting.
- 3.🥉 CyberGhost VPN το καλύτερο για νέους χρήστες — Εύκολο στη χρήση και εξαιρετικό για gaming.
- 4. NordVPN — Πραγματικά καλές λειτουργίες ασφαλείας και γρήγορες ταχύτητες σε κάθε διακομιστή
- 5. Surfshark — Εξαιρετικό για μεγάλες οικογένειες + απίστευτα προσιτά πακέτα.
- Επιλογές Νο#6-10 των καλύτερων VPN για το 2024.
- Γρήγορη σύγκριση των καλύτερων VPN για το 2024.
Επισήμανση συντακτών: Τα Intego, Private Internet Access, CyberGhost και ExpressVPN βρίσκονται υπό την ιδιοκτησία της Kape Technologies, της μητρικής μας εταιρείας.
🥇1. ExpressVPN — Το καλύτερο VPN για το 2024 Κορυφαία ασφάλεια, ταχύτητες και απόδοση
Το ExpressVPN είναι το γρηγορότερο VPN στον κλάδο, διαθέτει μερικές από τις πιο εύχρηστες εφαρμογές εκεί έξω και συνοδεύεται από κορυφαία χαρακτηριστικά ασφαλείας — κρυπτογράφηση AES 256-bit, μία επιβεβαιωμένη πολιτική μη διατήρησης αρχείων καταγραφής από ανεξάρτητο φορέα και έναν άψογο από πλευράς λειτουργίας διακόπτη έκτακτης ανάγκης (είναι ένα από τα λίγα VPN που διαθέτουν διακόπτη έκτακτης ανάγκης για κάθε κορυφαία πλατφόρμα). Επιπλέον, διαθέτει δικό του πρωτόκολλο VPN, προηγμένη αρχιτεκτονική διακομιστή, διαχωρισμό σήραγγας στις εφαρμογές για Windows, Android, δρομολογητές και Mac, ένα πρόγραμμα αποκλεισμού διαφημίσεων, ιχνηλάτισης και κακόβουλου λογισμικού για iOS, Mac και Linux καθώς και έναν δωρεάν διαχειριστή κωδικών πρόσβασης.
Μάλιστα, το ExpressVPN διαθέτει δική του ιδιωτική υπηρεσία κρυπτογράφησης DNS, η οποία παρέχει ένα επιπλέον επίπεδο ασφάλειας μέσω της κρυπτογράφησης των αιτημάτων DNS από τους διακομιστές του. Η τεχνολογία TrustedServer (Αξιόπιστος Διακομιστής) του ExpressVPN αποθηκεύει τα μεταδεδομένα διακομιστή στη μνήμη (RAM) των διακομιστών και όχι σε κάποιον σκληρό δίσκο. Αυτό σημαίνει ότι όλα τα προσωπικά σας δεδομένα καθαρίζονται με την επανεκκίνησή τους. Επίσης, υπάρχει και ο μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy), ο οποίος αλλάζει το κλειδί κρυπτογράφησης μετά από κάθε συνεδρία αποτρέποντας έτσι την παραβίαση μελλοντικών ή προηγούμενων κλειδιών σας από χάκερ.
Αν ψάχνετε κάποιο VPN για χρήση σε χώρες που υπόκεινται σε περιορισμούς, το ExpressVPN αποτελεί την καλύτερη επιλογή – αν ζείτε ή ταξιδεύετε σε μια χώρα με έντονη διαδικτυακή λογοκρισία, το ExpressVPN θα σας βοηθήσει να προσπελάσετε τα τείχη προστασίας και να ανακτήσετε την ελευθερία σας στο διαδίκτυο. Επιπλέον, το ExpressVPN συνιστά εξαιρετική επιλογή για streaming, torrenting και gaming – λειτουργεί με κάθε κορυφαίο ιστότοπο streaming, όπως είναι τα Netflix, Hulu και Disney+, αλλά και με λιγότερο γνωστούς ιστότοπους, όπως είναι τα FuboTV, RaiPlay και Crackle. Ακόμη, υποστηρίζει P2P κίνηση σε κάθε του διακομιστή και παρέχει τις πιο γρήγορες ταχύτητες για gaming εκεί έξω, προσφέροντας υποστήριξη για gaming στο Cloud.
Και έπειτα, υπάρχει το πρωτόκολλο Lightway του ExpressVPN, το οποίο είναι πιο αξιόπιστο και πιο γρήγορο, ενώ διατηρεί ισχυρότερη ασφάλεια σε σχέση με άλλα κορυφαία πρωτόκολλα VPN, όπως τα OpenVPN και WireGuard. Επιπλέον, το Lightway είναι ανοιχτού κώδικα, που σημαίνει ότι ο καθένας μπορεί να το επιθεωρήσει για τυχόν ελαττώματα ασφαλείας (έχει υποβληθεί και περάσει από εξωτερικό έλεγχο), ενώ χρησιμοποιεί το DTLS 1.3, την πιο πρόσφατη έκδοση του πρωτοκόλλου Datagram Transport Layer Security, το οποίο προστατεύει την επικοινωνία σε μη αξιόπιστα δίκτυα. Έτσι, επιτυγχάνεται καλύτερη ασφάλεια, απόκριση και απόδοση σε σύγκριση με άλλα πρωτόκολλα VPN. Στις δοκιμές μου, το Lightway αποδείχθηκε ότι είναι το ταχύτερο πρωτόκολλο VPN που έχω δοκιμάσει.
Είτε δοκιμάζετε ένα VPN για πρώτη φορά είτε είστε έμπειρος χρήστης, δεν θα αντιμετωπίσετε κανένα πρόβλημα κατά την πλοήγηση στην εύχρηστη εφαρμογή του ExpressVPN.
Θα χρειαστούν μονάχα μερικά λεπτά για την εγκατάστασή του σε οποιαδήποτε συσκευή. Οι διαδικασίες εύρεσης και σύνδεσης στον επιθυμητό διακομιστή είναι εύκολες, ενώ οι λειτουργίες του είναι εύκολο να εντοπιστούν και να χρησιμοποιηθούν. Και αν αντιμετωπίσετε προβλήματα, το ExpressVPN διαθέτει εξαιρετικές πλατφόρμες υποστήριξης πελατών, περιλαμβάνοντας φιλικούς και εξυπηρετικούς αντιπροσώπους σε ζωντανή συνομιλία, μια άμεσα ανταποκρίσιμη ομάδα email, αναλυτικούς οδηγούς εγκατάστασης και αντιμετώπισης προβλημάτων, καθώς και λεπτομερή πεδία συχνών ερωτήσεων (FAQ).
Το ExpressVPN επιτρέπει έως και 8 ταυτόχρονες συνδέσεις, ενώ δέχεται ένα ευρύ φάσμα μεθόδων πληρωμής (συμπεριλαμβανομένου του Bitcoin). Τέλος, διαθέτει εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών χωρίς κανέναν κίνδυνο.
ExpressVPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 105
- Πρωτόκολλα: Lightway, IKEv2/IPSec, OpenVPN UDP/TCP, L2TP/IPSec
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Απόκρυψης (Obfuscation), διαχωρισμού σήραγγας
- Προστασία διαρροών: DNS, WebRTC, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
ExpressVPN δοκιμές ταχύτητας
Με διακομιστές VPN σε 105 χώρες, συμπεριλαμβανομένης της Ελλάδας, το ExpressVPN προσφέρει ένα από τα πιο εκτεταμένα δίκτυα σε αυτήν τη λίστα — ενώ διαθέτει τουλάχιστον 15 χώρες με διακομιστές σε διάφορες πόλεις. Για παράδειγμα, οι ΗΠΑ διαθέτουν 20+ τοποθεσίες διακομιστή (σε Νέα Υόρκη, Σικάγο, Σολτ Λέικ Σίτι, Λος Άντζελες κλπ.), ενώ το Ηνωμένο Βασίλειο διαθέτει 5 διαφορετικές τοποθεσίες (Ντόκλαντς, Ανατολικό Λονδίνο, Λονδίνο, Μίντλαντς και Γουέμπλεϊ). Η ομάδα μου κι εγώ δοκιμάσαμε από μία σύνδεση σε κάθε χώρα, ενώ στην περίπτωση των χωρών με πολλαπλές τοποθεσίες διακομιστή δοκιμάσαμε κάθε διαθέσιμη πόλη.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Χρησιμοποίησα το Smart Location (Έξυπνη Τοποθεσία) του ExpressVPN, το οποίο επιλέγει τον κορυφαίο διακομιστή για την τοποθεσία σας. Συνδέθηκα σε κάθε διακομιστή σχεδόν άμεσα διατηρώντας εξαιρετικά γρήγορες ταχύτητες — ακόμη και σε τοποθεσίες που απείχαν περισσότερο από 16.000 χιλιόμετρα από τον τοπικό μου διακομιστή. Οι εν λόγω υψηλές ταχύτητες οφείλονται στο πρωτόκολλο Lightway του ExpressVPN, το οποίο απέδωσε πολύ καλύτερα από οποιοδήποτε άλλο πρωτόκολλο VPN (συμπεριλαμβανομένου του WireGuard).
Συνολικά, το ExpressVPN μείωσε την ταχύτητά μου κατά μέσο όρο μόνο 15% — τιμή σημαντικά καλύτερη από τους περισσότερους ανταγωνιστές.
ExpressVPN streaming: Ισχυρό
Το ExpressVPN αποτελεί την κορυφαία επιλογή μου για streaming. Λειτουργεί με 100+ υπηρεσίες streaming, συμπεριλαμβάνοντας δημοφιλείς επιλογές, όπως τα Netflix, Hulu, HBO Max και Disney+, ANT1, SKAI TV, ALPHA TV, καθώς και λιγότερο γνωστές υπηρεσίες, όπως τα Kodi, Sling TV και FuboTV. Διαθέτουμε μία διεθνή ομάδα δοκιμαστών, καθένας εκ των οποίων μας επιβεβαίωσε ότι το ExpressVPN λειτουργεί με τις διαθέσιμες υπηρεσίες streaming των χωρών τους. Στις δοκιμές μου, παρακολούθησα απροβλημάτιστα ταινίες και τηλεοπτικές εκπομπές σε ποιότητα HD και 4K στα Netflix US, Hulu, YouTube US καθώς και σε άλλες εφαρμογές streaming. Επιπλέον, η λειτουργία MediaStreamer του ExpressVPN σας επιτρέπει να κάνετε streaming από συσκευές που δεν διαθέτουν εφαρμογή VPN, όπως είναι το Roku, ορισμένες smart TV (Apple TV) και κονσόλες παιχνιδιών.

ExpressVPN torrenting: Ισχυρό
Το ExpressVPN υποστηρίζει κοινή χρήση αρχείων P2P και torrenting σε όλους τους διακομιστές του σε 100+ χώρες — σε αντίθεση με πολλά άλλα κορυφαία VPN, τα οποία υποστηρίζουν torrenting μόνο σε ειδικούς διακομιστές P2P (κοινής χρήσης αρχείων). Επίσης, λειτουργεί με όλα τα κορυφαία προγράμματα torrenting, συμπεριλαμβανομένων των BitTorrent, uTorrent, Deluge, Vuze και άλλων (είχα τις πιο γρήγορες ταχύτητες λήψης με το BitTorrent).
Μάλιστα, δεν χρειάζεται να ανησυχείτε για τυχόν διαρροή της διεύθυνσης IP σας κατά τη διάρκεια του torrenting — προτού ξεκινήσω να κατεβάζω αρχεία, πραγματοποίησα δοκιμές διαρροής DNS, WebRTC και IPv6 σε 20+ χώρες και δεν εντόπισα τίποτα.
Επιπλέον, το ExpressVPN διαθέτει διαχωρισμό σήραγγας — επιτρέποντάς σας διαδικτυακή κίνηση (μόνο για εφαρμογές) τόσο μέσω του VPN όσο και μέσω του τοπικού σας διακομιστή. Μου αρέσει πολύ το εργαλείο διαχωρισμού σήραγγας του ExpressVPN, επειδή είναι πολύ εύκολο στη χρήση και στην πλοήγηση. Χρησιμοποιώ συχνά τη λειτουργία διαχωρισμού σήραγγας κατά τη διάρκεια του torrenting για να κατευθύνω αποκλειστικά τις εφαρμογές P2P (κοινής χρήσης αρχείων) μέσω του VPN και να αυξήσω τις ταχύτητες λήψης.
Ακόμη, το ExpressVPN είναι ένα από τα ελάχιστα VPN που προσφέρει διαχωρισμό σήραγγας για Mac συσκευές (macOS 10.15 και μεταγενέστερες εκδόσεις). Το Private Internet Access είναι το άλλο VPN της λίστας με διαχωρισμό σήραγγας για macOS (για όλες τις εκδόσεις).
Ακόμη, ο πάροχος επιτρέπει την προώθηση θυρών (port forwarding), δίνοντάς σας έτσι τη δυνατότητα να συνδεθείτε με περισσότερους ομότιμους (peers) για ταχύτερες λήψεις. Ωστόσο, μπορείτε να ενεργοποιήσετε τη συγκεκριμένη λειτουργία μόνο μέσω της εφαρμογής δρομολογητή του ExpressVPN — ευτυχώς, η εγκατάσταση καθώς και η χρήση αυτής είναι πολύ απλή και εύκολη.
ExpressVPN Gaming: Ισχυρό
Το ExpressVPN είναι το καλύτερο VPN για gaming στην αγορά αυτή τη στιγμή. Το χρησιμοποίησα για να παίξω Dota 2, Fortnite, PUBG και Counter-Strike: Global Offensive ενώ ήμουν συνδεδεμένος σε έναν διακομιστή στη χώρα που έχω επισκεφθεί αυτήν τη στιγμή (ΗΠΑ) και σε έναν απομακρυσμένο διακομιστή στην Αυστραλία, έχοντας μια πολύ ομαλή εμπειρία — στον απομακρυσμένο διακομιστή, διατήρησα τυπικές τιμές στο ping και δεν αντιμετώπισα επιβραδύνσεις ή τυχαίες αποσυνδέσεις.
Επίσης, μου αρέσει που όλοι οι διακομιστές του ExpressVPN διαθέτουν προστασία έναντι επιθέσεων DDoS (Distributed Denial of Service), οι οποίες μπορούν να σας θέσουν εκτός σύνδεσης — έτσι, ακόμα κι αν ένας θυμωμένος ηττημένος προσπαθούσε να σας επιτεθεί την ώρα που είστε συνδεδεμένος στο ExpressVPN, δεν θα κατάφερνε τίποτα.
Επιπλέον, το ExpressVPN είναι ένα από τα λίγα VPN με ειδική εφαρμογή για δρομολογητή, την οποία μπορείτε να εγκαταστήσετε με ευκολία στον δρομολογητή σας, ώστε να χρησιμοποιήσετε το VPN για να παίξετε από συσκευές που δεν υποστηρίζουν εγγενώς VPN (π.χ. κονσόλες παιχνιδιών). Το ExpressVPN διαθέτει χρήσιμες οδηγίες που σας δείχνουν πώς να ρυθμίσετε την εφαρμογή δρομολογητή του, με την όλη διαδικασία να μην διαρκεί περισσότερο από 7–8 λεπτά — η εφαρμογή δρομολογητή είναι εξαιρετικά εύχρηστη και απλή στην πλοήγηση. Εναλλακτικά, μπορείτε να αποκτήσετε τον δρομολογητή του ExpressVPN που φέρει προεγκατεστημένο το VPN.
Ακόμη, με το ExpressVPN λαμβάνετε υποστήριξη σε Cloud gaming πλατφόρμες, δηλαδή σε υπηρεσίες που μεταδίδουν παιχνίδια σε smartphone, tablet και άλλες φορητές συσκευές. Το ExpressVPN παρέχει υποστήριξη για πολλές υπηρεσίες Cloud gaming, συμπεριλαμβανομένων των Google Stadia, GeForce Now και PlayStation Now. Απόλαυσα ομαλή ροή, όταν δοκίμασα το ExpressVPN στον λογαριασμό μου στο PlayStation Now.
ExpressVPN παράκαμψη λογοκρισίας: Ισχυρό
Το ExpressVPN διαθέτει διακομιστές απόκρυψης (obfuscation) που έχουν σχεδιαστεί με σκοπό να σας βοηθήσουν να ανακτήσετε τη διαδικτυακή σας ελευθερία παρακάμπτοντας τα τείχη προστασίας. Χάρη στην υψηλού επιπέδου ασφάλειά του, το ExpressVPN αποτελεί τον ευκολότερο, ταχύτερο και ασφαλέστερο τρόπο για να αντιμετωπίσετε τους περιορισμούς και τους αποκλεισμούς VPN. Οι διακομιστές απόκρυψης του ExpressVPN βρίσκονται σε ολόκληρο τον κόσμο, επομένως οι χρήστες σε χώρες με έντονη λογοκρισία μπορούν να βρουν έναν διακομιστή σε μια κοντινή χώρα για να αποκτήσουν μεγαλύτερες ταχύτητες. Για παράδειγμα, οι χρήστες στην Ινδονησία μπορούν να συνδεθούν σε έναν διακομιστή στη Σιγκαπούρη. Οι χρήστες στην Κίνα μπορούν να συνδεθούν σε οποιονδήποτε διακομιστή, ωστόσο, το ExpressVPN διαθέτει μια προτεινόμενη λίστα τοποθεσιών για να παρέχει τις καλύτερες και πιο αξιόπιστες συνδέσεις. Ενώ το ExpressVPN συνιστά τη χρήση του πρωτοκόλλου Automatic για την παράκαμψη των τειχών προστασίας, όλα τα πρωτόκολλά του λειτουργούν στις περισσότερες χώρες.
ExpressVPN πακέτα και τιμολόγηση
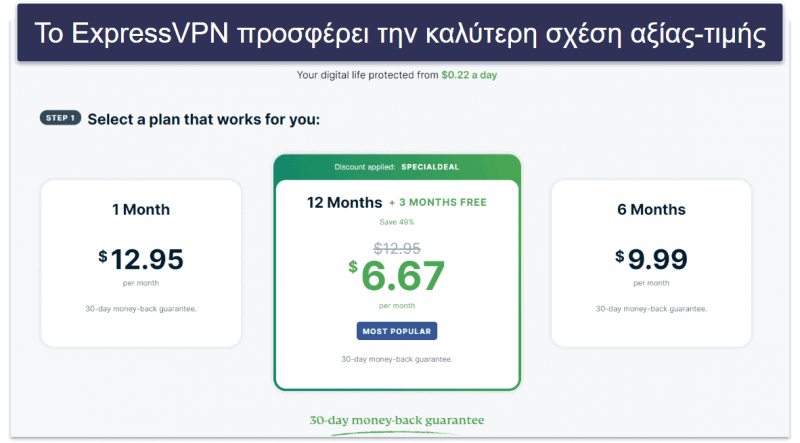
Το ExpressVPN προσφέρει μερικά μηνιαία πακέτα καθώς και ένα ετήσιο. Αν και είναι λίγο ακριβότερο από ορισμένους παρόχους σε αυτήν τη λίστα, έχει την καλύτερη απόδοση με εξαιρετικά χαρακτηριστικά ασφάλειας, ταχύτητας και απορρήτου (διαθέτοντας και ισχυρές δυνατότητες περί streaming). Το καλό είναι ότι μπορείτε να λάβετε 63% έκπτωση στο ετήσιο πακέτο με το κόστος του να ανέρχεται σε μόλις 5,49 $ / το μήνα. Επίσης, το ExpressVPN δίνει κατά καιρούς 3 μήνες δωρεάν χρήσης. Έτσι, μπορείτε πραγματικά να λάβετε συνολικά 15 μήνες.
Το ExpressVPN δέχεται πληρωμές σε ποικίλες μορφές, συμπεριλαμβανομένων 7 διαφορετικών πιστωτικών καρτών, PayPal, Bitcoin και διαφόρων διαδικτυακών τραπεζικών υπηρεσιών — εφαρμογές όπως τα Mint, Qiwi, iDeal, Sofort και άλλα. Κάθε πακέτο υποστηρίζεται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση τουl ExpressVPN >
🥈2. Private Internet Access (PIA) — Ευέλικτο, γρήγορο και πολύ εύχρηστο Εξαιρετικό για streaming και torrenting
Το Private Internet Access (PIA) είναι ασφαλές, διατηρεί γρήγορες ταχύτητες σε όλους τους διακομιστές και παρέχει εξαιρετική υποστήριξη streaming και torrenting. Στις δοκιμές μου, το PIA λειτούργησε με όλες τις δημοφιλείς υπηρεσίες streaming, όπως είναι το Netflix US, το Hulu, το Disney+ US, καθώς και με πολλές ακόμη, ενώ δεν υπήρχε καθόλου επιβράδυνση ή buffering κατά τη διάρκειας αναπαραγωγής περιεχομένου.
Επίσης, το PIA είναι εξαιρετικό για torrenting, καθώς υποστηρίζει διαδικτυακή κίνηση P2P (κοινή χρήση αρχείων) σε κάθε διακομιστή, συνεργάζεται με όλα τα κορυφαία προγράμματα torrent και διαθέτει προώθηση θυρών (port forwarding), επιτρέποντάς σας να συνδεθείτε απευθείας με ομότιμους (peers) για να αποκτήσετε μεγαλύτερες ταχύτητες λήψης. Επιπλέον, το PIA λειτουργεί πολύ καλά σε χώρες με περιορισμούς (μεγάλη λογοκρισία και τείχη προστασίας).
Το PIA διαθέτεις τις πιο ευέλικτες και προσαρμόσιμες εφαρμογές σε σύγκριση με οποιοδήποτε άλλο VPN αυτής της λίστας. Οι εφαρμογές του είναι καλά σχεδιασμένες, εξαιρετικά εύχρηστες και προσφέρουν μία ντουζίνα επιλογών εξατομίκευσης στους προχωρημένους χρήστες — διαφορετικά επίπεδα κρυπτογράφησης, επιτρεπόμενη λίστα IP και εφαρμογών, συνδέσεις τοπικών θυρών, αυτοματοποιημένους κανόνες και πολλά άλλα. Ακόμη, μου αρέσει που ο πάροχος επιτρέπει απεριόριστες συνδέσεις, δίνοντάς σας έτσι τη δυνατότητα να εγκαταστήσετε και να χρησιμοποιήσετε τις εφαρμογές του σε όσες συσκευές επιθυμείτε.
Αναφορικά με τις τοποθεσίες διακομιστή, το PIA διαθέτει διακομιστές σε 90+ χώρες (συμπεριλαμβανομένης της Ελλάδας) και είναι το μοναδικό VPN στην αγορά που έχει διακομιστή και στις 50 πολιτείες των ΗΠΑ. Έτσι, μπορείτε να συνδεθείτε στον διακομιστή της προτίμησής σας για να λάβετε τις καλύτερες ταχύτητες.
Αυτό που μου αρέσει περισσότερο στο PIA είναι η ισχυρή δέσμευσή του για το απόρρητο των χρηστών του — ενώ τα περισσότερα VPN ισχυρίζονται ότι δεν καταγράφουν τα δεδομένα χρήστη (αλλά δεν μπορούν να υποστηρίξουν πρακτικά τον εν λόγω ισχυρισμό), οι ισχυρισμοί του Private Internet Access περί μη καταγραφής των δεδομένων χρήστη έχουν αποδειχθεί αληθείς μέσω ανεξάρτητων ελέγχων και πολλών δικαστικών υποθέσεων. Το PIA δημοσιεύει ακόμη και τακτικές αναφορές διαφάνειας όπου επισημαίνεται η μη παραγωγή αρχείων καταγραφής προς τις αρχές, ενώ οι εφαρμογές του είναι ανοιχτού κώδικα.
Αναφορικά με την ασφάλεια, το PIA διαθέτει διακομιστές τεχνολογίας RAM, μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy), διακόπτη έκτακτης ανάγκης (διαθέσιμο σε iOS), καθώς και δικό του DNS. Ο διαχωρισμός σήραγγας διατίθεται σε Android, Windows, Mac και Linux, και σας επιτρέπει να εξαιρέσετε εφαρμογές και διευθύνσεις IP ιστότοπων (το ExpressVPN επιτρέπει μόνο την εξαίρεση εφαρμογών). Επίσης, το PIA διαθέτει ένα πολύ καλό και φιλικό προς τον χρήστη πρόγραμμα αποκλεισμού διαφημίσεων (PIA MACE) που αποκλείει τους ιχνηλάτες και αποτρέπει την επίσκεψή σας σε δυνητικά κακόβουλους ιστότοπους
Το PIA επιτρέπει απεριόριστες ταυτόχρονες συνδέσεις και υποστηρίζει κάθε αγορά με μία εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Private Internet Access στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 91
- Πρωτόκολλα: OpenVPN, WireGuard, IKEv2/IPSec (μόνο σε iOS)
- Κρυπτογράφηση δεδομένων: 128-bit AES, 256-bit AES
- Εξειδικευμένοι διακομιστές: Απόκρυψης (Obfuscation), διαχωρισμού σήραγγας, SOCKS5, Streaming, αποκλειστικών IP
- Προστασία διαρροών: DNS, WebRTC, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
Private Internet Access δοκιμές ταχύτητας
Το PIA αναφέρει την απόκριση για κάθε διακομιστή στο δίκτυό του, βοηθώντας σας έτσι να επιλέξετε τον ταχύτερο διακομιστή. Στις δοκιμές μου επέλεξα τον διακομιστή με τη χαμηλότερη απόκριση καθώς έλεγχα την ταχύτητα σύνδεσης του PIA ανά χώρα.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Το PIA παρέχει αρκετά γρήγορες ταχύτητες στο διαδίκτυο. Όταν δοκίμασα το PIA, η ταχύτητά μου μειώθηκε μόνο κατά 6% στους ταχύτερους διακομιστές. Ωστόσο, όταν συνδέθηκα σε ορισμένους διακομιστές του PIA στην Ασία και στη Νότια Αμερική, η ταχύτητά μου μειώθηκε κατά περίπου 40%, τιμή η οποία εξακολουθεί να είναι πολύ καλύτερη από τον μέσο όρο. Συνολικά, το PIA επιβράδυνε τη σύνδεσή μου στο διαδίκτυο κατά περίπου 22% — περισσότερο σε σχέση με το ExpressVPN αλλά και πάλι λιγότερο από τους περισσότερους ανταγωνιστές.
Private Internet Access streaming: Ισχυρό
Το PIA είναι εξαιρετικό για streaming. Λειτουργεί με όλες τις δημοφιλείς υπηρεσίες streaming, καθώς και με πολλές λιγότερο γνωστές υπηρεσίες. Στις δοκιμές μου, λειτούργησε με όλες τις διαθέσιμες υπηρεσίες streaming της τοποθεσίας μου, συμπεριλαμβανομένων των Netflix US, Amazon Prime US, Hulu, Disney+ US, Pluto TV (στις ΗΠΑ), USA Network, VRV και πολλών άλλων ιστότοπων streaming. Επίσης, το PIA διαθέτει ειδικά βελτιστοποιημένους διακομιστές για streaming σε τουλάχιστον 7 χώρες (συμπεριλαμβανομένων των ΗΠΑ, του Ηνωμένου Βασιλείου, της Ιταλίας και της Ιαπωνίας), οι οποίοι έχουν σχεδιαστεί για να λειτουργούν με συγκεκριμένες διεθνείς εφαρμογές streaming, συμπεριλαμβανομένων των Netflix, Disney+, Amazon Prime και BBC iPlayer, αλλά και με τοπικές υπηρεσίες streaming, όπως τα RaiPlay (Ιταλία), Crunchyroll (ΗΠΑ), HBO Nordic (Δανία) και Ruutu (Φινλανδία).
Επίσης, το PIA διαθέτει Smart DNS, το οποίο σας επιτρέπει να μεταδώσετε ταινίες και τηλεοπτικές εκπομπές σε συσκευές που δεν διαθέτουν εφαρμογή VPN (κάτι παρόμοιο με το MediaStreamer του ExpressVPN).

Private Internet Access torrenting: Ισχυρό
Όπως το ExpressVPN, έτσι και το PIA επιτρέπει το torrenting σε κάθε διακομιστή σε 91+ χώρες. Επομένως, δεν θα χρειαστεί να αναζητήσετε ή να συνδεθείτε σε έναν αποκλειστικό διακομιστή P2P (κοινής χρήσης αρχείων), όπως θα κάνετε με ορισμένα άλλα VPN (το PIA είναι ένα από τα αγαπημένα torrenting VPN που έχω δοκιμάσει). Δοκίμασα διάφορους διακομιστές του PIA σε ολόκληρο τον κόσμο με τα uTorrent και BitTorrent μη αντιμετωπίζοντας πρόβλημα με την κοινή χρήση αρχείων στα εν λόγω προγράμματα torrent.
Επίσης, μου αρέσει το εργαλείο πολλαπλών βημάτων (multi-hop) SOCKS5 του PIA, το οποίο δρομολογεί τη σύνδεσή σας μέσω ενός διακομιστή μεσολάβησης, ο οποίος μπορεί να αυξήσει ελαφρώς τις ταχύτητες torrenting. Επιπλέον, είναι υπέροχο που το PIA διαθέτει προώθηση θυρών (port forwarding) — αλλά είναι κρίμα που, σε αντίθεση με το ExpressVPN, δεν υποστηρίζει την προώθηση θυρών στους διακομιστές του στις ΗΠΑ.
Υπέβαλα το PIA σε πολλαπλές δοκιμές διαρροής DNS με αυτό να περνά επιτυχώς κάθε έλεγχο χωρίς καμία διαρροή. Ακόμη, μου αρέσει πολύ η αυτόματη απενεργοποίηση της διαδικτυακής κίνησης IPv6 του PIA — δεν χρειάστηκε να ανησυχήσω για τη χειροκίνητη απενεργοποίησή του (όπως συνέβη με το VyprVPN).
Private Internet Access gaming: Συνήθως ισχυρό
To PIA είναι ένα από τα καλύτερα gaming VPN το 2024, προσφέροντας πολύ ισχυρή ασφάλεια και γρήγορες συνδέσεις — στις δοκιμές μου, το ping μου δεν άλλαξε ποτέ κατά τη διάρκεια του παιχνιδιού μου σε έναν τοπικό διακομιστή VPN. Και παρότι είχα ελαφρώς υψηλότερο ping απ’ ό,τι με το ExpressVPN την ώρα που έπαιζα σε έναν απομακρυσμένο διακομιστή VPN, οι gaming συνεδρίες μου παρέμειναν ομαλές.
Επιπλέον, όλοι οι διακομιστές του PIA διαθέτουν προστασία έναντι επιθέσεων DDoS. Μάλιστα, μπορείτε να συνδέσετε το PIA στον δρομολογητή σας και, στη συνέχεια, να παίξετε παιχνίδια στην Xbox ή PlayStation κονσόλα σας. Ωστόσο, θα χρειαστεί να πραγματοποιήσετε μία χειροκίνητη ρύθμιση στην προκειμένη περίπτωση — ευτυχώς, το PIA παρέχει πρόσβαση σε αναλυτικούς οδηγούς που σας δείχνουν τι πρέπει να κάνετε. Ακόμα κι έτσι, νομίζω ότι η εφαρμογή δρομολογητή του ExpressVPN είναι πιο βολική, αφού απαιτείται λιγότερος χρόνος για τη ρύθμισή του και είναι ευκολότερο στη χρήση.
Το PIA δεν αναφέρει εάν παρέχει υποστήριξη για gaming στο Cloud — επικοινώνησα με το τμήμα υποστήριξης πελατών με τους αντιπροσώπους του να μου αναφέρουν ότι δεν εγγυώνται τη λειτουργία του PIA με Cloud gaming πλατφόρμες. Στις δοκιμές μου, λειτούργησε αρκετά καλά, αλλά δεν μπορώ να υποσχεθώ ότι θα λειτουργήσει το ίδιο καλά και για εσάς. Εάν σκοπεύετε να χρησιμοποιήσετε ένα VPN κυρίως για gaming στο Cloud, τότε σας προτείνω να κοιτάξετε το ExpressVPN, αφού παρέχει υποστήριξη για πολλαπλές Cloud gaming πλατφόρμες.
Private Internet Access παράκαμψη λογοκρισίας: Ισχυρό
Το PIA χρησιμοποιεί το πρωτόκολλο Shadowsocks και τη λειτουργία Multi-hop για να παρακάμψει τα τείχη προστασίας — το εν λόγω πρωτόκολλο αποκρύπτει τη χρήση του VPN, ώστε να επισκέπτεστε ελεύθερα οποιονδήποτε περιορισμένο-από πλευράς πρόσβασης-ιστότοπο. Το Shadowsocks είναι εύκολο να εντοπιστεί [βρίσκεται στην ενότητα «Proxy» στο μενού Settings (Ρυθμίσεις)] και ενεργοποιείται απλά με ένα κλικ. Το PIA σας δίνει την επιλογή να συνδεθείτε σε 7 διαφορετικές χώρες (επιλέξτε αυτή που βρίσκεται πιο κοντά στην τοποθεσία σας) μεταξύ των οποίων οι ΗΠΑ, η Ιαπωνία και το Ισραήλ, ώστε να «πηδήξετε» πάνω από το τείχος προστασίας.
Private Internet Access πακέτα και τιμολόγηση
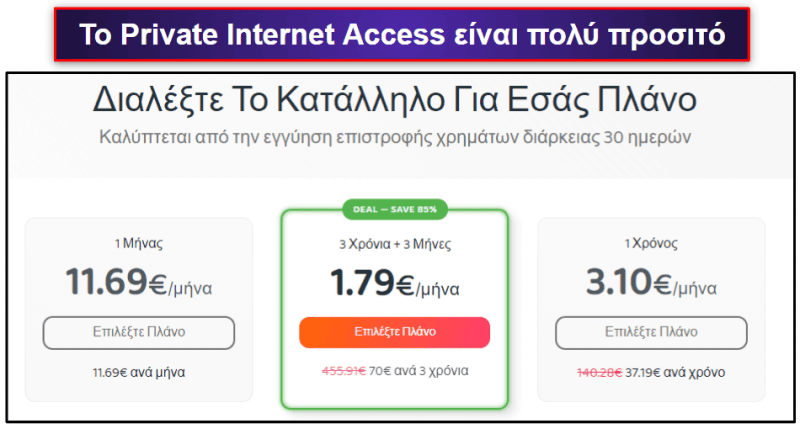
Το PIA διαθέτει 3 επί πληρωμή πακέτα, τα οποία φέρουν λογική τιμολόγηση — βασικά, το PIA είναι ένα από τα φθηνότερα VPN εκεί έξω, με τα πακέτα του να ξεκινούν από μόλις 2,03 $ / το μήνα. Επίσης, το PIA προσφέρει μηνιαία πρόσθετα, όπως Antivirus και αποκλειστική διεύθυνση IP.
Το PIA δέχεται πιστωτικές κάρτες, PayPal και κρυπτονομίσματα, όπως Bitcoin, Ethereum και Litecoin. Επίσης, μου αρέσει η δυνατότητα πληρωμής μέσω δωροκάρτας της Amazon, η οποία θα σας βοηθήσει να παραμείνετε εντελώς ανώνυμοι. Τέλος, το PIA καλύπτει κάθε πακέτο του με εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση του Private Internet Access >
Επισήμανση συντακτών: Το Private Internet Access και ο εν λόγω ιστότοπος βρίσκονται υπό κοινή ιδιοκτησία.
🥉3. CyberGhost VPN — Υψηλή απόδοση με μεγάλο δίκτυο διακομιστών (Συνιστάται για gaming)
Το CyberGhost VPN διαθέτει ένα από τα μεγαλύτερα δίκτυα διακομιστών στην αγορά, αριθμώντας 8.000+ διακομιστές σε 100 χώρες, με τοποθεσίες διακομιστή ακόμη και στην Αθήνα. Έτσι, εξασφαλίζετε γρήγορες ταχύτητες, καθώς αποφεύγετε φαινόμενα υπερφορτωμένων διακομιστών, ενώ μπορείτε να συνδεθείτε σε τοπικούς ή κοντινούς διακομιστές για ακόμη πιο γρήγορες συνδέσεις — κατά μέσο όρο, αντιμετώπισα επιβράδυνση της τάξεως του 32% μόνο, τιμή αρκετά καλή.
Επίσης, ο πάροχος αποτελεί μία καλή επιλογή για gaming, καθώς έρχεται με 70+ αποκλειστικούς διακομιστές για gaming σε 4 χώρες (ΗΠΑ, Ηνωμένο Βασίλειο, Γερμανία και Γαλλία). Οι εν λόγω διακομιστές είναι ειδικά βελτιστοποιημένοι, ώστε να παρέχουν σταθερό ping και ομαλές συνδέσεις — στις δοκιμές μου, πάντοτε είχα γρήγορες gaming συνεδρίες καθώς έπαιζα Dota 2 και Counter-Strike: Global Offensive.
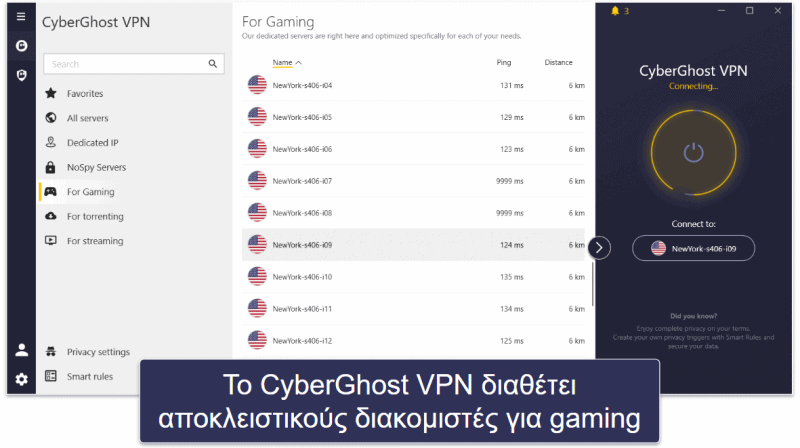
Επιπλέον, το CyberGhost VPN φέρει πολύ καλή υποστήριξη streaming, καθώς διαθέτει 100+ αποκλειστικούς διακομιστές για streaming σε 20+ χώρες, οι οποίοι είναι ειδικά βελτιστοποιημένοι για 50+ πλατφόρμες streaming. Μεταξύ αυτών περιλαμβάνονται τα Netflix, Amazon Prime, Disney+, CBC, France TV, RaiPlay, DAZN και ITV.
Επίσης, παρέχει εξαιρετική υποστήριξη P2P (κοινή χρήση αρχείων), αφού διαθέτει 8.500+ διακομιστές P2P σε 70+ χώρες. Είναι κρίμα που δεν επιτρέπει το torrenting σε όλους τους διακομιστές του, όπως συμβαίνει στα ExpressVPN και PIA, αλλά το δίκτυο διακομιστών P2P του εξακολουθεί να είναι μεγαλύτερο από τους περισσότερους ανταγωνιστές.
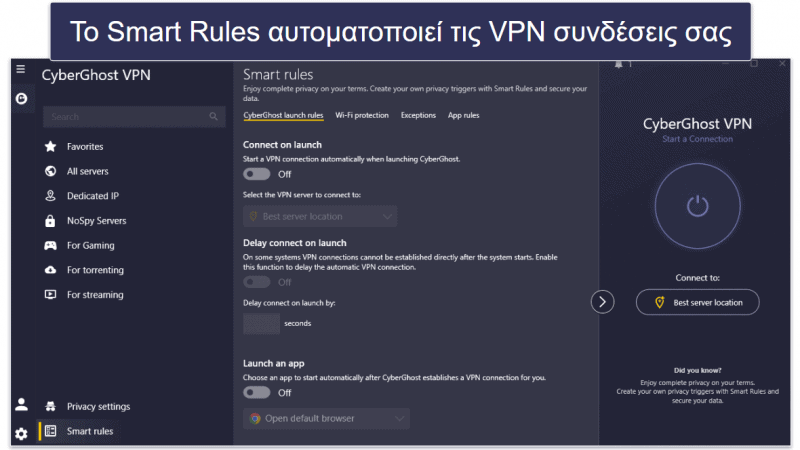
Λατρεύω τη λειτουργία Smart Rules (Έξυπνοι Κανόνες) του CyberGhost VPN, η οποία διατίθεται σε σταθερούς υπολογιστές και επιτρέπει την αυτοματοποίηση των προτιμήσεων σύνδεσης VPN, τους κανόνες προστασίας δικτύου Wi-Fi καθώς και την επιλογή των ιστότοπων που θα δρομολογούνται μέσω της σήραγγας VPN. Για παράδειγμα, μπορείτε να χρησιμοποιήσετε το Smart Rules για να ρυθμίσετε την αυτόματη σύνδεση της εφαρμογής VPN σε έναν συγκεκριμένο διακομιστή streaming και το άνοιγμα μιας εφαρμογής streaming κατά την εκκίνηση. Εναλλακτικά, μπορείτε να διαμορφώσετε το CyberGhost VPN, ώστε να συνδέεται αυτόματα με τον ταχύτερο διακομιστή καθώς ανοίγετε μια συγκεκριμένη εφαρμογή (π.χ. ένα πρόγραμμα-πελάτη gaming).
Ακόμη, το συγκεκριμένο VPN προσφέρει πραγματικά ισχυρές λειτουργίες ασφαλείας — διαθέτει προηγμένα χαρακτηριστικά, όπως ολοκληρωμένη προστασία διαρροών, διακομιστές τεχνολογίας RAM και μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy). Επίσης, διαθέτει διακομιστές NoSpy, οι οποίοι παρέχουν επιπλέον ασφάλεια και απόρρητο, αφού μόνο το προσωπικό του παρόχου διαθέτει πρόσβαση σε αυτούς. Επιπλέον, υπάρχει το Content Blocker (Αποκλειστής Περιεχομένου), το οποίο σας προστατεύει από κακόβουλους ιστότοπους, αν και δεν θα σας απαλλάξει από τις διαφημίσεις το ίδιο αποτελεσματικά με το PIA MACE του Private Internet Access.
Το CyberGhost VPN επιτρέπει 7 συνδέσεις και συνοδεύει όλα τα μακροπρόθεσμα πακέτα του με εγγύηση επιστροφής χρημάτων διάρκειας 45 ημερών. Επίσης, καλύπτει το μικρότερο-χρονικά-πακέτο του με εγγύηση επιστροφής χρημάτων 14 ημερών.
CyberGhost VPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 100
- Πρωτόκολλα: OpenVPN, IKEv2/IPSec, WireGuard
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: NoSpy, P2P, streaming, gaming
- Προστασία διαρροών: DNS, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
CyberGhost VPN δοκιμές ταχύτητας
Το CyberGhost VPN διαθέτει 8.000+ διακομιστές σε 100 χώρες — περισσότερους από σχεδόν κάθε άλλο πάροχο VPN. Εγώ και η ομάδα μου δοκιμάσαμε την ταχύτητα σύνδεσης του CyberGhost VPN σε κάθε χώρα.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Αν και το CyberGhost VPN δεν είναι τόσο γρήγορο όσο τα ExpressVPN και Private Internet Access, είχα μέση μείωση της ταχύτητάς μου κατά 32% — τιμή καλύτερη από αρκετούς ανταγωνιστές. Μάλιστα, ήμουν σε θέση να παίξω παιχνίδια χωρίς καθυστέρηση σε κάθε διακομιστή που δοκίμασα (ακόμη και στους πιο απομακρυσμένους).
CyberGhost VPN streaming: Ισχυρό
Το CyberGhost VPN διαθέτει 100+ διακομιστές streaming σε 20+ χώρες. Ένας εκπρόσωπος από το τμήμα υποστήριξης πελατών επιβεβαίωσε ότι οι εν λόγω διακομιστές είναι ειδικά βελτιστοποιημένοι για να λειτουργούν με 50+ υπηρεσίες streaming. Για παράδειγμα, υπάρχει ένας συγκεκριμένος διακομιστής στις ΗΠΑ για το Hulu και ένας άλλος διακομιστής στις ΗΠΑ που λειτουργεί με το Amazon Prime. Ομοίως, εάν ζείτε στο Ηνωμένο Βασίλειο, υπάρχει ένας διακομιστής στο Ηνωμένο Βασίλειο που είναι ειδικά βελτιστοποιημένος για το Netflix UK (υπάρχουν αποκλειστικοί διακομιστές για το Netflix σε 15+ χώρες). Κατά τη διάρκεια των δοκιμών μου, παρακολούθησα ταινίες και ντοκιμαντέρ στα Netflix US, Hulu, καθώς και σε άλλες υπηρεσίες που διατίθενται στη χώρα μου, σε HD ποιότητα χωρίς καμία διακοπή!

CyberGhost VPN torrenting: Ισχυρό
Το CyberGhost VPN επιτρέπει το torrenting σε 8.500+ διακομιστές σε 100+ χώρες από ολόκληρο τον κόσμο. Έτσι, μπορείτε να βρείτε έναν διακομιστή P2P (κοινής χρήσης αρχείων) κοντά στην τοποθεσία σας, ο οποίος θα σας προσφέρει γρήγορες ταχύτητες ανεξαρτήτως του πού βρίσκεστε. Επίσης, μου αρέσει πολύ που το CyberGhost VPN παρουσιάζει την απόσταση του P2P διακομιστή από εσάς — απλά, επιλέξτε τον πλησιέστερο διακομιστή για να αποκτήσετε τις μεγαλύτερες δυνατές ταχύτητες λήψης.
CyberGhost VPN gaming: Συνήθως ισχυρό
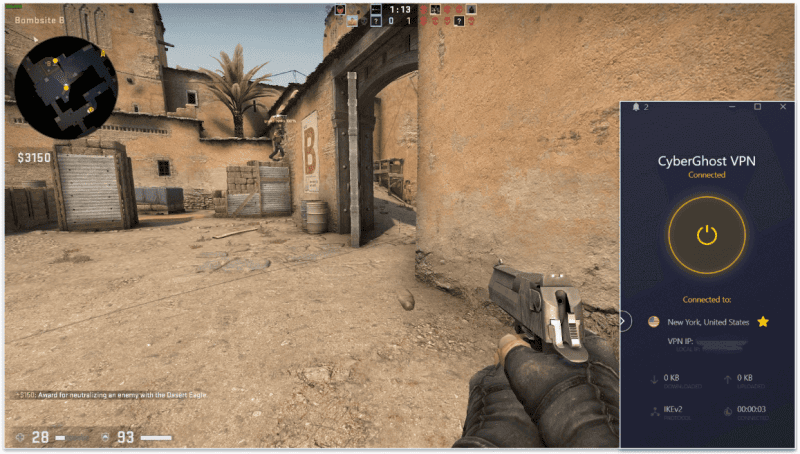
Το CyberGhost VPN παρέχει μια εξαιρετική εμπειρία παιχνιδιού όντας ένα από τα καλύτερα VPN για gaming εκεί έξω. Στις δοκιμές μου, το CyberGhost VPN μου παρείχε πραγματικά ομαλό gaming – το ping μου δεν ήταν ποτέ πολύ υψηλό (ακόμη και σε απομακρυσμένους διακομιστές), δεν αντιμετώπισα καμία καθυστέρηση ή «κόλλημα» και οι συνδέσεις μου δεν διακόπηκαν ποτέ.
Επίσης, μου αρέσει πολύ που το CyberGhost VPN προσφέρει πρόσβαση σε 90+ αποκλειστικούς διακομιστές για gaming σε 4 χώρες (ΗΠΑ, Ηνωμένο Βασίλειο, Γερμανία και Γαλλία), οι οποίοι έχουν βελτιστοποιηθεί για να παρέχουν σταθερή και γρήγορη εμπειρία παιχνιδιού. Όταν έπαιξα ένα παιχνίδι στο Dota 2 χρησιμοποιώντας τον γερμανικό διακομιστή για gaming, το ping μου ήταν μεταξύ 108–112 ms, τιμή ελαφρώς χαμηλότερη από αυτήν που μου προσέφερε ένας τυπικός γερμανικός διακομιστής.
Όλοι οι διακομιστές του CyberGhost VPN διαθέτουν προστασία DDoS. Επίσης, μπορείτε να ρυθμίσετε το CyberGhost VPN στον δρομολογητή σας ακολουθώντας τις οδηγίες του παρόχου (είναι αρκετά χρήσιμες και περιλαμβάνουν σχετικές εικόνες) — αλλά νομίζω ότι είναι πιο βολικό να χρησιμοποιήσετε το ExpressVPN στον δρομολογητή σας, καθώς συνοδεύεται από μια αποκλειστική εφαρμογή δρομολογητή που είναι πολύ απλή στη ρύθμιση και στη χρήση.
Ακόμη, ρώτησα τους αντιπροσώπους του CyberGhost VPN εάν το VPN είναι συμβατό με πλατφόρμες παιχνιδιών στο Cloud. Δυστυχώς, μου ανέφεραν ότι δεν μπορούν να εγγυηθούν τη λειτουργία του VPN. Στις δοκιμές μου, το CyberGhost λειτούργησε με Cloud Gaming πλατφόρμες, ωστόσο, θα πρέπει να έχετε κατά νου ότι μπορεί να μην ισχύσει το ίδιο και για εσάς — αν σκοπεύετε να χρησιμοποιήσετε το VPN κυρίως για gaming στο Cloud, δοκιμάστε το ExpressVPN, το οποίο παρέχει υποστήριξη για gaming στο Cloud.
CyberGhost VPN παράκαμψη λογοκρισίας: Αδύναμο
Σε αντίθεση με τα ExpressVPN και Private Internet Access, το CyberGhost δεν διαθέτει διακομιστές απόκρυψης (obfuscation), επομένως δεν αποτελεί την καλύτερη επιλογή VPN για την αντιμετώπιση της διαδικτυακής λογοκρισίας σε χώρες με περιορισμούς. Ωστόσο, αν δεν ζείτε ή δεν σχεδιάζετε να ταξιδέψετε σε μια χώρα που υπόκειται σε διαδικτυακούς περιορισμούς, το CyberGhost VPN εξακολουθεί να αποτελεί μία καλή επιλογή για gaming, streaming, torrenting, ενώ παράλληλα διατηρεί εσάς και την περιήγησή σας στο διαδίκτυο ανώνυμα.
CyberGhost VPN πακέτα και τιμολόγηση
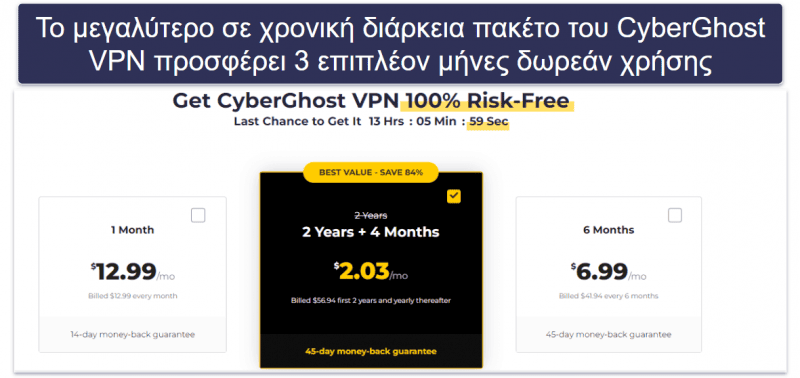
Το CyberGhost VPN προσφέρει διάφορα πακέτα, μεταξύ των οποίων ένα μηνιαίο πακέτο, που είναι αρκετά ακριβό (12,99 $ / το μήνα), και ένα πολυετές πακέτο, το οποίο αποτελεί μία από τις καλύτερες προσφορές εκεί έξω (2,19 $ / το μήνα). Το πολυετές πακέτο δεν είναι μονάχα φθηνό, αλλά συχνά περιλαμβάνει και αρκετούς μήνες δωρεάν χρήσης. Το μηνιαίο πακέτο υποστηρίζεται από εγγύηση επιστροφής χρημάτων διάρκειας 14 ημερών, ενώ τα μακροπρόθεσμα πακέτα περιλαμβάνουν μια πολύ γενναιόδωρη εγγύηση επιστροφής χρημάτων διάρκειας 45 ημερών. Το CyberGhost δέχεται πληρωμές με πιστωτικές κάρτες, PayPal και Bitcoin.
Διαβάστε την πλήρη αξιολόγηση του CyberGhost VPN >
Επισήμανση συντακτών: Το CyberGhost και ο εν λόγω ιστότοπος βρίσκονται υπό κοινή ιδιοκτησία.
4. NordVPN — Εξαιρετικές δυνατότητες ασφαλείας και γρήγορες ταχύτητες σε όλους τους διακομιστές
Το NordVPN παρέχει πρόσβαση σε πολλαπλές λειτουργίες ασφαλείας, οι οποίες διατηρούν τα δεδομένα σας ασφαλή στο διαδίκτυο — διαθέτει προηγμένα χαρακτηριστικά ασφαλείας, όπως ολοκληρωμένη προστασία διαρροών, διακομιστές αποκλειστικής τεχνολογίας RAM και μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy). Η αυστηρή πολιτική μη καταγραφής έχει ελεγχθεί από ανεξάρτητους φορείς (όπως ισχύει και στην περίπτωση των ExpressVPN και Private Internet Access) και αποδείχθηκε αληθής, όταν ένας διακομιστής από ένα κέντρο δεδομένων υπέστη παραβίαση δεδομένων (όπου κανένα στοιχείο χρήστη δεν παραβιάστηκε).
Επίσης, το NordVPN διαθέτει το Threat Protection (Προστασία Απειλών), ένα από τα καλύτερα προγράμματα αποκλεισμού διαφημίσεων VPN στην αγορά, το οποίο σας απαλλάσσει από κακόβουλες διαφημίσεις, αποκλείει συνδέσεις σε ύποπτους ιστότοπους και προστατεύει τη συσκευή σας από λήψεις που έχουν μολυνθεί από κακόβουλα λογισμικά. Μάλιστα, το Threat Protection παραμένει ενεργό ακόμα κι όταν δεν είστε συνδεδεμένοι σε έναν διακομιστή VPN.
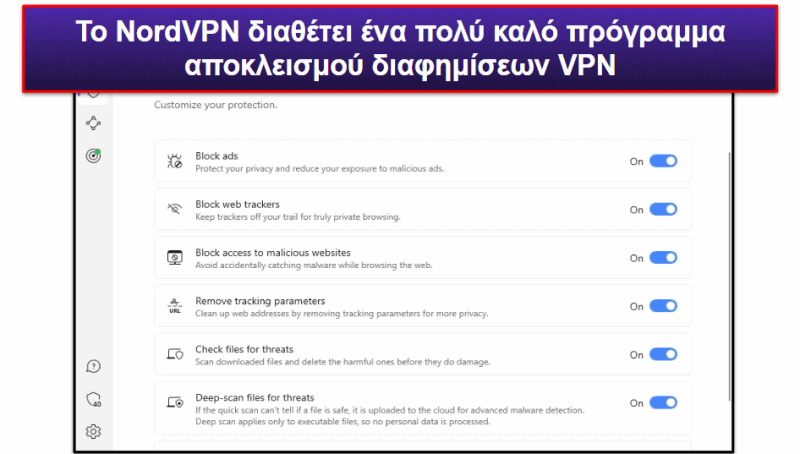
Επιπλέον, το NordVPN διαθέτει διπλούς διακομιστές VPN, οι οποίοι προσθέτουν ένα επιπλέον επίπεδο κρυπτογράφησης στέλνοντας τη διαδικτυακής σας κίνηση μέσω 2 διακομιστών VPN αντί για 1. Μάλιστα, διαθέτει λειτουργία απόκρυψης (obfuscation), η οποία σας επιτρέπει να αποκρύψετε τη VPN κίνησή σας από τον πάροχο υπηρεσιών διαδικτύου (ISP) σας.
Ακόμη, το συγκεκριμένο VPN διαθέτει ένα ιδιόκτητο πρωτόκολλο, το NordLynx, το οποίο σχεδιάστηκε με γνώμονα την παροχή ισχυρής ασφάλειας και υψηλών ταχυτήτων.
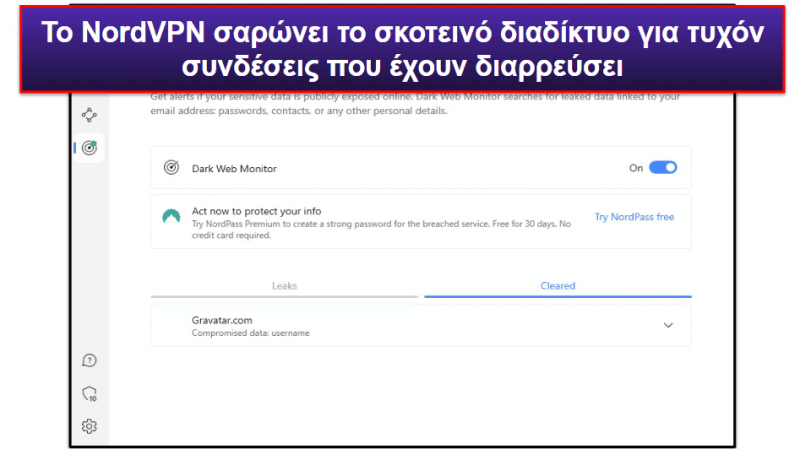
Επιπροσθέτως, το NordVPN είναι ένα από τα λίγα VPN της αγοράς που διαθέτει λειτουργία παρακολούθησης σκοτεινού διαδικτύου (Dark Web Monitor), η οποία σαρώνει το σκοτεινό διαδίκτυο και σας ειδοποιεί σε περίπτωση διαρροής των στοιχείων σύνδεσής σας που σχετίζονται με τον λογαριασμό σας στο NordVPN.
Ο πάροχος είναι εξαιρετικός για streaming και torrenting — λειτουργεί με πολλές δημοφιλείς υπηρεσίες streaming, όπως είναι τα Netflix και BBC iPlayer, και διαθέτει 4.500+ διακομιστές P2P (κοινής χρήσης αρχείων). Ακόμη, παρέχει πολύ καλές ταχύτητες για streaming, torrenting και άλλες διαδικτυακές δραστηριότητες σε κάθε διακομιστή του.
Πιστεύω ότι το NordVPN είναι ένα καλό VPN για gaming χάρη στη λειτουργία Meshnet που διαθέτει, η οποία σας επιτρέπει να συνδέσετε έως και 60 συσκευές μέσω κρυπτογραφημένων συνδέσεων VPN — η εν λόγω λειτουργία θα σας βοηθήσει να φιλοξενήσετε εικονικά LAN πάρτι με ασφάλεια.
Επίσης, το εν λόγω VPN φέρει πολλά ακόμη προνόμια — διαθέτει 5.400+ διακομιστές σε 60 χώρες, διαχωρισμό σήραγγας καθώς και πραγματικά έξυπνες εφαρμογές για κάθε κορυφαία πλατφόρμα.
Το NordVPN επιτρέπει 10 συνδέσεις, διαθέτει επί πληρωμή πακέτα καθώς και αρκετές συνδρομές πολλαπλών επιπέδων, ενώ καλύπτει όλες τις αγορές του με εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
NordVPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 111
- Πρωτόκολλα: NordLynx, OpenVPN, IKEv2/IPSec
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Απόκρυψης (obfuscation), διπλό VPN, Onion μέσω VPN, αποκλειστικών IP
- Προστασία διαρροών: DNS, WebRTC, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
NordVPN δοκιμές ταχύτητας
Δοκίμασα έναν τυχαίο διακομιστή σε καθεμία από τις 60 χώρες του NordVPN για να συγκρίνω τις ταχύτητές του σε σχέση με τους ανταγωνιστές.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Συνολικά, το NordVPN απέδωσε πολύ καλά στις δοκιμές μου. Αν και μείωσε τις ταχύτητες μου κατά περίπου 12% στους κοντινότερους διακομιστές (που είναι λίγο περισσότερο από τα ExpressVPN και Private Internet Access), εξακολούθησε να μου παρέχει γρήγορες ταχύτητες για περιήγηση, streaming και gaming. Στους απομακρυσμένους διακομιστές αντιμετώπισα επιβράδυνση της τάξεως του 37% κατά μέσο όρο μόνο — είχα γρήγορες ταχύτητες σε κάθε διαδικτυακή μου δραστηριότητα και αντιμετώπισα μονάχα ορισμένες μικρές επιβραδύνσεις σε μερικούς διακομιστές.
NordVPN streaming: Ισχυρό
Η υποστήριξη πελατών του NordVPN επιβεβαίωσε ότι λειτουργεί με 10+ υπηρεσίες streaming, μεταξύ των οποίων και κορυφαίοι ιστότοποι, όπως τα Netflix, Amazon Prime, Disney+, Max και BBC iPlayer. Επίσης, το smart DNS του παρόχου σας επιτρέπει να κάνετε streaming σε συσκευές που δεν υποστηρίζουν VPN, όπως ορισμένες smart TV και κονσόλες παιχνιδιών.

NordVPN torrenting: Ισχυρό
Το NordVPN επιτρέπει το torrenting σε 4.500+ διακομιστές σε 45+ χώρες, ώστε να μην υπάρξει περίπτωση να κατεβάσετε torrent σε υπερφορτωμένους διακομιστές που μπορεί να επιβραδύνουν τις ταχύτητες σας. Δοκίμασα τον συγκεκριμένο πάροχο με δημοφιλείς εφαρμογές P2P (κοινής χρήσης αρχείων), όπως τα uTorrent και Vuze, και δεν αντιμετώπισα ποτέ προβλήματα.
Επίσης, με το NordVPN αποκτάτε πρόσβαση σε διακομιστές μεσολάβησης SOCKS5 σε 3 χώρες (ΗΠΑ, Ολλανδία και Σουηδία). Οι εν λόγω διακομιστές αλλάζουν τη διεύθυνση IP σας όπως κάνει ένα VPN, αλλά δεν χρησιμοποιούν κρυπτογράφηση, ώστε να έχετε σημαντικά μεγαλύτερες ταχύτητες λήψης — στις δοκιμές μου, οι ταχύτητες P2P μου ήταν 25% υψηλότερες, όταν χρησιμοποίησα έναν διακομιστή μεσολάβησης SOCKS5 αντί για έναν διακομιστή VPN.
Όπως συναντάται στο ExpressVPN, το NordVPN συνοδεύεται από ολοκληρωμένη προστασία διαρροών — πραγματοποίησα δοκιμές διαρροής ενώ ήμουν συνδεδεμένος με διακομιστές σε 10+ χώρες προτού ξεκινήσω τη λήψη torrent και δεν αντιμετώπισα κανένα φαινόμενο διαρροής.
Ακόμη, μου άρεσε η λειτουργία Threat Protection (Προστασία Απειλών) του NordVPN — μπορεί να σας προστατεύσει από κακόβουλες λήψεις P2P, καθώς σαρώνει εκτελέσιμα αρχεία μεγέθους έως 20 MB για τυχόν κακόβουλο λογισμικό. Επιπλέον, μπορεί να σας απαλλάξει από ενοχλητικές διαφημίσεις σε ιστότοπους P2P.
NordVPN gaming: Ισχυρό
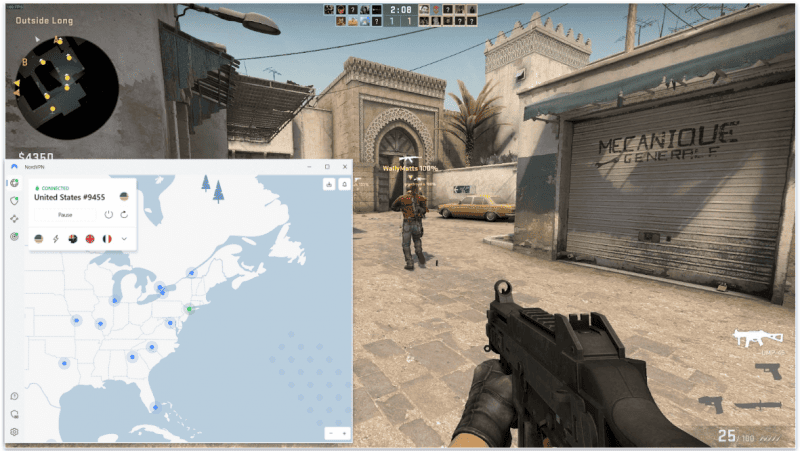
Το NordVPN παρέχει εξαιρετική υποστήριξη gaming, αφού προσφέρει ομαλές ταχύτητες σύνδεσης — στις δοκιμές μου, είχα πολύ καλό και σταθερό ping σε τοπικούς διακομιστές, ενώ παρέμεινε σε συνηθισμένες τιμές και σταθερό τη στιγμή που έπαιζα σε απομακρυσμένους διακομιστές. Επίσης, δεν αντιμετώπισα καμία διακοπή σύνδεσης. Αν και αντιμετώπισα καθυστέρηση κατά το gaming σε απομακρυσμένους διακομιστές, αυτή ήταν πολύ μικρή και δεν εμπόδισε το παιχνίδι μου.
Ο πάροχος αποτρέπει τις επιθέσεις DDoS (αλλά στερείται προστασίας DDoS), ενώ επιτρέπει την αυτόματη ρύθμιση σε πολλά μοντέλα δρομολογητών — επίσης, διαθέτει χρήσιμες οδηγίες καθιστώντας τη διαδικασία εγκατάστασης αρκετά απλή. Παρ’ όλα αυτά, νομίζω ότι το ExpressVPN φέρει καλύτερη υποστήριξη δρομολογητή, καθώς συνοδεύεται από μια αποκλειστική εφαρμογή δρομολογητή που είναι απλή στην εγκατάσταση αλλά και στη χρήση.
Δυστυχώς, οι εκπρόσωποι του NordVPN δεν μπόρεσαν να μου εγγυηθούν τη λειτουργία του VPN με Cloud gaming πλατφόρμες – δεν αντιμετώπισα προβλήματα κατά τη χρήση του NordVPN σε πλατφόρμες όπως το Google Stadia, ωστόσο, αυτό δεν σημαίνει πως κι εσείς θα έχετε τα ίδια αποτελέσματα με εμένα. Εάν είστε λάτρης του Cloud gaming, σας προτείνω να επιλέξετε το ExpressVPN, καθώς συνοδεύεται από υποστήριξη gaming στο Cloud.
Ακόμη, μου αρέσει πολύ η δυνατότητα Meshnet του NordVPN — μπορείτε να τη χρησιμοποιήσετε για να διοργανώσετε εικονικά LAN πάρτι και να προστατεύσετε τη σύνδεσή σας στις συσκευές των φίλων σας χρησιμοποιώντας κρυπτογράφηση VPN. Επιπλέον, το Meshnet χρησιμοποιεί το πρωτόκολλο NordLynx του παρόχου, το οποίο παρέχει πραγματικά γρήγορες ταχύτητες.
NordVPN παράκαμψη λογοκρισίας: Αδύναμο
Δυστυχώς, το NordVPN δεν συνιστά την καλύτερη επιλογή ως προς την παράκαμψη των τειχών προστασίας σε χώρες που υπόκεινται σε περιορισμούς, αφού δεν λειτουργεί σε περιοχές όπως η Κίνα, η Ρωσία και το Ιράν. Άλλοι κορυφαίοι ανταγωνιστές, όπως τα ExpressVPN και Private Internet Access, αποτελούν πολύ καλύτερες επιλογές στην προκειμένη περίπτωση.
NordVPN πακέτα και τιμολόγηση
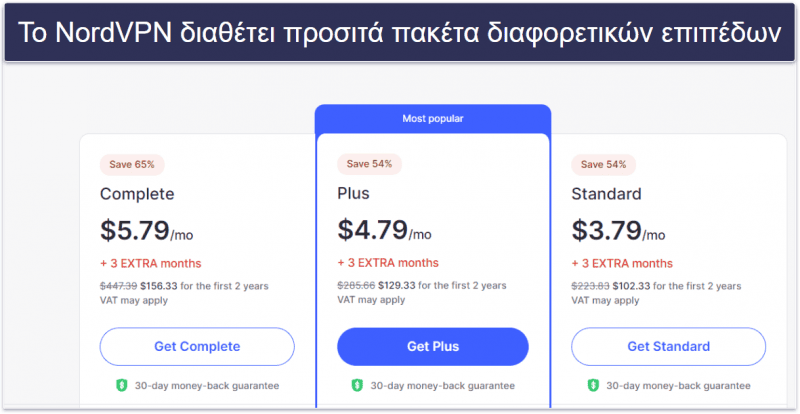
Το NordVPN διαθέτει επί πληρωμή πακέτα διάρκειας 1 μήνα, 1 έτους και 2 ετών, καθώς και διαφορετικές συνδρομές πολλαπλών επιπέδων: Standard, Plus και Complete.
Το πακέτο Standard ξεκινά από τα 3,39 $ / το μήνα και παρέχει πρόσβαση σε κάθε λειτουργία VPN του παρόχου.
Το πακέτο Plus ξεκινά από τα 3,89 $ / το μήνα και προσφέρει επιπλέον το NordPass, έναν αρκετά καλό διαχειριστή κωδικών πρόσβασης.
Τέλος, το πακέτο Complete ξεκινά από τα 5,39 $ / το μήνα προσφέροντας επιπλέον το NordLocker, το οποίο σας παρέχει μία κρυπτογραφημένη αποθήκευση στο Cloud.
Το NordVPN δέχεται διάφορους τρόπους πληρωμής, συμπεριλαμβανομένων πιστωτικών/χρεωστικών καρτών, PayPal και κρυπτονομισμάτων. Επίσης, καλύπτει κάθε αγορά με εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση του NordVPN >
5. Surfshark — Εξαιρετικά προσιτό VPN
Το Surfshark είναι ένα από τα πιο προσιτά VPN της αγοράς, με πακέτα που ξεκινούν από μόλις 1,99 $ / το μήνα — επομένως, αποτελεί μια καλή επιλογή, αν έχετε περιορισμένο προϋπολογισμό.
Το Surfshark διαθέτει πολύ καλά χαρακτηριστικά ασφαλείας, μεταξύ των οποίων το CleanWeb, ένα πολύ καλό πρόγραμμα αποκλεισμού διαφημίσεων — στις δοκιμές μου, απαλλάχθηκα από τις περισσότερες διαφημίσεις στα μέσα ενημέρωσης, αν και το εν λόγω εργαλείο δεν ήταν πάντοτε σε θέση να αποκλείσει αναδυόμενες διαφημίσεις (σε αντίθεση με το PIA MACE του Private Internet Access και το Threat Protection του NordVPN). Το θετικό στην προκειμένη περίπτωση, είναι ότι πάντοτε απέτρεπε τη σύνδεσή μου σε ύποπτους ιστότοπους HTTP.
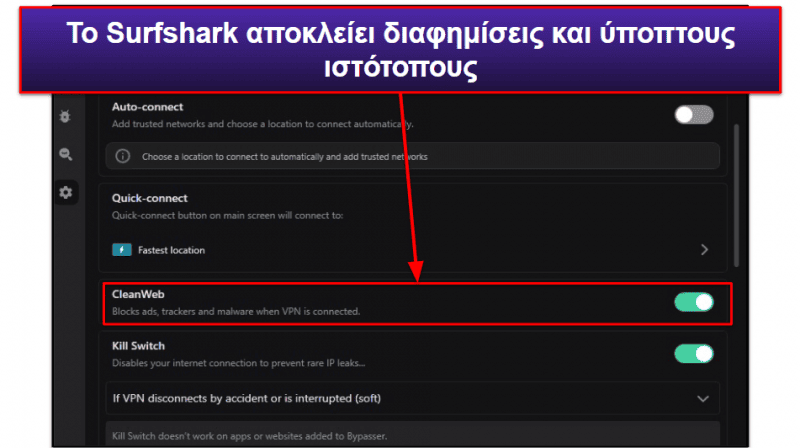
Επιπλέον, παρέχει λειτουργία απόκρυψης (obfuscation), διπλές συνδέσεις VPN για πρόσθετη ασφάλεια και το IP Rotator (Εναλλάκτης IP), μία λειτουργία που αλλάζει τακτικά τη διεύθυνση IP σας με σκοπό την αποτροπή της παρακολούθησης της τοποθεσία σας από τρίτους. Ακόμη, ο πάροχος φέρει ελεγμένη πολιτική μη τήρησης αρχείων καταγραφής και προηγμένα χαρακτηριστικά ασφαλείας, όπως διακομιστές αποκλειστικής τεχνολογίας RAM και μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy) — ωστόσο, σε αντίθεση με τα ExpressVPN και Private Internet Access, στερείται ολοκληρωμένης προστασίας διαρροών (αν και δεν αντιμετώπισα καμία διαρροή στις δοκιμές μου).
Το Surfhsark υποστηρίζει λήψεις P2P σε κάθε διακομιστή του, ενώ διαθέτει πολύ καλή υποστήριξη streaming, αφού το VPN του λειτουργεί με κορυφαίους ιστότοπους, όπως τα Netflix, Max και BBC iPlayer — αν και δεν λειτούργησε με το Disney+.
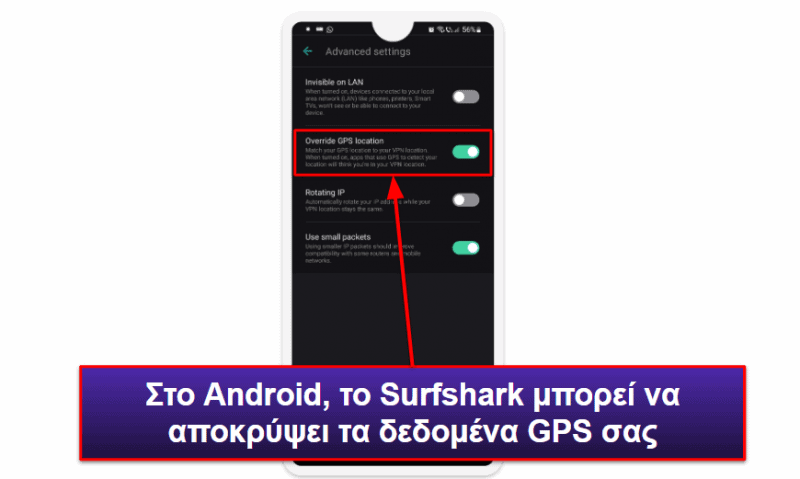
Στα επιπλέον θετικά, μου αρέσει η λειτουργία Override GPS Location (Παράκαμψη Τοποθεσίας GPS) στο Android. Αυτή η καταπληκτική λειτουργία αντιστοιχίζει τα GPS δεδομένα σας με τη διεύθυνση IP που έχει εκχωρηθεί από το VPN για να αποτρέψει τις εφαρμογές streaming (για κινητά) να εντοπίσουν τη VPN σύνδεσή σας. Με αυτόν τον τρόπο, μπορείτε να παρακολουθήσετε περιεχόμενο ροής μέσα από την εφαρμογή για κινητά της εκάστοτε πλατφόρμας streaming αντί από τον ιστότοπό της (όπως πρέπει να κάνετε στα περισσότερα VPN).
Το Surfshark διαθέτει 3.200+ διακομιστές σε 100+ χώρες, καθιστώντας εύκολη τη χρήση κοντινών διακομιστών για γρήγορες ταχύτητες. Ο πάροχος προσφέρει γρήγορες συνδέσεις στους περισσότερους διακομιστές, αλλά αντιμετώπισα σημαντικές επιβραδύνσεις σε πολύ απομακρυσμένους διακομιστές. Στα θετικά του εν λόγω VPN εντάσσονται οι εύχρηστες εφαρμογές και η δυνατότητα απεριόριστων συνδέσεων.
Το Surfshark συνοδεύει κάθε επί πληρωμή πακέτο του με εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Surfshark στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 100
- Πρωτόκολλα: WireGuard, OpenVPN, IKEv2/IPSec
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Δυναμικοί πολλαπλών βημάτων (Dynamic Multihop), P2P, αποκλειστικών IP
- Προστασία διαρροών: DNS
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
Surfshark δοκιμές ταχύτητας
Πραγματοποίησα μια δοκιμή ταχύτητας σε έναν τυχαίο διακομιστή σε καθεμία από τις 100 χώρες του Surfshark για να δω ποιες είναι οι μέσες ταχύτητες του VPN μου.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Γενικά, το Surfshark μου παρείχε καλές ταχύτητες σχεδόν σε κάθε του διακομιστή. Μείωσε τις ταχύτητες μου κατά περίπου 13% στους πλησιέστερους διακομιστές, δηλαδή περισσότερο από τα ExpressVPN και Private Internet Access, ωστόσο, εξακολουθούσα να απολαμβάνω γρήγορες ταχύτητες σε όλες τις διαδικτυακές δραστηριότητες — μάλιστα, συνέχισα να διατηρώ τις εν λόγω ταχύτητες σε κοντινούς διακομιστές αλλά και σε ορισμένους απομακρυσμένους διακομιστές. Μονάχα σε πολύ απομακρυσμένους διακομιστές αντιμετώπισα πολύ αισθητές επιβραδύνσεις (84% κατά μέσο όρο).
Επίσης, το Surfshark διαθέτει έναν ενσωματωμένο έλεγχο ταχύτητας που σας επιτρέπει να δοκιμάσετε τους διακομιστές του για να δείτε ποιοι παρέχουν τις μεγαλύτερες ταχύτητες. Ωστόσο, αξίζει να επισημανθεί ότι η εν λόγω λειτουργία δεν είναι πολύ ακριβής (επιπλέον, είναι κάπως άβολη στη χρήση).
Surfshark streaming: Συνήθως ισχυρό
Το Surfshark είναι ένα αρκετά καλό VPN για streaming, αφού λειτουργεί με τις πιο δημοφιλείς υπηρεσίες streaming, συμπεριλαμβάνοντας διαφορετικές βιβλιοθήκες των Netflix, Amazon Prime και Max. Ο συνάδελφός μας στο Ηνωμένο Βασίλειο επιβεβαίωσε ότι λειτουργεί και με το BBC iPlayer. Δυστυχώς, δεν λειτουργεί με το Disney+ σε αντίθεση με τα ExpressVPN και Private Internet Access. Επίσης, ο πάροχος διαθέτει ένα smart DNS, μέσω του οποίου μπορείτε να επισκεφθείτε υπηρεσίες streaming (μόνο από τις ΗΠΑ) σε συσκευές που δεν υποστηρίζουν VPN.
Επιπλέον, το Surfshark είναι ένα από τα ελάχιστα VPN που διαθέτει λειτουργία, η οποία σας επιτρέπει να αντιστοιχίσετε την GPS τοποθεσία σας με τη διεύθυνση IP σας — η λειτουργία αυτή είναι διαθέσιμη μόνο σε Android και σας δίνει τη δυνατότητα να παρακολουθήσετε βίντεο μέσω streaming από streaming εφαρμογές για κινητά (συνήθως κάτι τέτοιο είναι εφικτό μονάχα από τους σχετικούς ιστότοπους streaming).

Surfshark torrenting: Συνήθως ισχυρό
Το Surfshark παρέχει καλή υποστήριξη torrenting, καθώς επιτρέπει λήψεις P2P (κοινής χρήσης αρχείων) σε όλους τους διακομιστές του. Παρ’ όλα αυτά, ο εκπρόσωπος του Surfshark προτείνει τη χρήση των αποκλειστικών διακομιστών P2P που είναι διαθέσιμοι σε 100+ χώρες — μπορείτε να τους βρείτε πληκτρολογώντας «P2P» στη γραμμή αναζήτησης της εφαρμογής. Επίσης, δοκίμασα το Surfshark με δημοφιλή προγράμματα P2P, όπως τα qBittorrent και Vuze, και λειτούργησε απροβλημάτιστα. Ωστόσο, είναι πραγματικά κρίμα που ο πάροχος στερείται άλλων σχετικών λειτουργιών κοινής χρήσης αρχείων, όπως είναι η προώθηση θυρών.
Μάλιστα, διενήργησα δοκιμές διαρροής προτού ξεκινήσω το torrenting μη εντοπίζοντας διαρροές με το Surfshark – αν και δεν διαθέτει ολοκληρωμένη προστασία διαρροών, όπως το ExpressVPN και το Private Internet Access.
Ακόμη, μου αρέσει ο τρόπος που η λειτουργία CleanWeb σας προστατεύει από κακόβουλους ιστότοπους P2P — μάλιστα, αυτή μπορεί να σας απαλλάξει από την πλειοψηφία των διαφημίσεων σε διακομιστές torrent.
Surfshark gaming: Συνήθως ισχυρό
Το Surfshark είναι πολύ καλό για gaming, αφού διατήρησε καθ’ όλη τη διάρκεια των δοκιμών μου καλές ταχύτητες σε κοντινούς διακομιστές – το ping μου ήταν συνεχώς πολύ χαμηλό και σταθερό. Ωστόσο, αντιμετώπισα υψηλό ping και καθυστέρηση κατά το παιχνίδι σε απομακρυσμένους διακομιστές, τα οποία εμπόδισαν σε ορισμένες περιπτώσεις το παιχνίδι μου.
Επίσης, ο πάροχος διαθέτει προστασία DDoS και υποστηρίζει ρυθμίσεις σε πολλά μοντέλα δρομολογητών. Παρ’ όλα αυτά, αν θέλετε ένα VPN για τον δρομολογητή σας προκειμένου να παίξετε, σας προτείνω να δοκιμάσετε το ExpressVPN, το οποίο διαθέτει εγγενή εφαρμογή δρομολογητή που είναι πολύ εύκολη στην εγκατάσταση και στη χρήση.
Αξίζει να σημειωθεί ότι το Surfshark δεν εγγυάται τη λειτουργία της υπηρεσίας του σε Cloud gaming πλατφόρμες — λειτούργησε στις δοκιμές μου, αλλά δεν μπορώ να υποσχεθώ ότι θα έχετε κι εσείς τα ίδια αποτελέσματα. Σε περίπτωση που ασχολείστε με το Cloud gaming, δοκιμάστε το ExpressVPN, μιας και αυτό παρέχει υποστήριξη για Cloud gaming υπηρεσίες.
Surfshark παράκαμψη λογοκρισίας: Αδύναμο
Το Surfshark δεν λειτουργεί σε χώρες που υπόκεινται σε περιορισμούς, όπως η Ρωσία, η Κίνα και η Ινδονησία – 10+ εκπρόσωποι του τμήματος υποστήριξης επιβεβαίωσαν το παραπάνω. Εάν χρειάζεστε ένα VPN που λειτουργεί σταθερά σε περιοριστικές περιοχές, τότε σας προτείνω τα ExpressVPN και Private Internet Access.
Surfshark πακέτα και τιμολόγηση
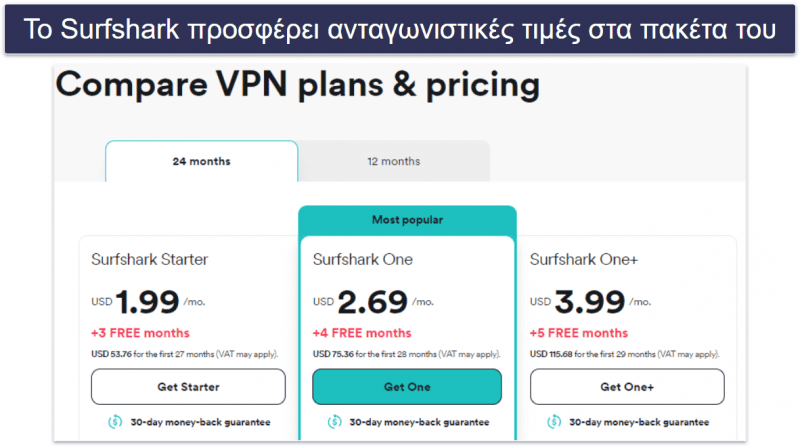
Το Surfshark διαθέτει συνδρομές 3 επιπέδων και πολύ προσιτά επί πληρωμή πακέτα, περιλαμβάνοντας πακέτα διάρκειας 1 μήνα, 1 έτους και 2 ετών — νομίζω ότι το Surfshark Starter θα φανεί αρκετό για τους περισσότερους χρήστες VPN, ενώ το μακροχρόνιο πακέτο του παρέχει την καλύτερη σχέση αξία-τιμής ξεκινώντας από μόνο 1,99 $ / το μήνα, τιμή αρκετά φθηνή, ενώ συνοδεύεται από 2 μήνες δωρεάν χρήσης. Ο πάροχος αποδέχεται διάφορους τρόπους πληρωμής, όπως πιστωτικές/χρεωστικές κάρτες, PayPal, Google Pay, Amazon Pay και κρυπτονομίσματα. Ακόμη, υποστηρίζει κάθε αγορά με μία εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση του Surfshark >
6. PrivateVPN — Καλό VPN για streaming
Το PrivateVPN είναι γρήγορο, ασφαλές και διαθέτει καλή υποστήριξη streaming. Το δοκίμασα στο Netflix US, στο Hulu αλλά και σε μερικούς ακόμη ιστότοπους περιεχομένου που διατίθενται στις ΗΠΑ. Κατάφερα να επισκεφθώ όλα τα παραπάνω έχοντας σταθερά γρήγορες ταχύτητες, ενώ παρακολούθησα βίντεο σε HD ποιότητα χωρίς καμία απολύτως διακοπή.
Επίσης, το PrivateVPN υποστηρίζει το torrenting σε κάθε του διακομιστή, ενώ παράλληλα λειτουργεί με όλα τα δημοφιλή προγράμματα torrenting.

Εκτός από τις τυπικές λειτουργίες ασφαλείας, όπως είναι η κρυπτογράφηση AES 256-bit, τα πολλαπλά πρωτόκολλα σύνδεσης και ο διακόπτης έκτακτης ανάγκης, το PrivateVPN περιλαμβάνει πρόσθετες λειτουργίες, όπως λειτουργία απόκρυψης (obfuscation), ώστε να αποφεύγετε τους αποκλεισμούς VPN και τους διαδικτυακούς περιορισμούς σε χώρες που λογοκρίνουν το διαδίκτυο. Επιπλέον, προσφέρει υποστήριξη στο Tor προσφέροντας έτσι ένα επιπλέον επίπεδο ασφάλειας κατά την περιήγηση στο δίκτυο του Tor. Σε αντίθεση με άλλους κορυφαίους ανταγωνιστές, όπως τα ExpressVPN και Private Internet Access, το PrivateVPN δεν διαθέτει διαχωρισμό σήραγγας.
Ένας λογαριασμός στο PrivateVPN καλύπτει 10 συσκευές, με όλα τα πακέτα να καλύπτονται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών, ενώ διατίθενται ευέλικτες επιλογές πληρωμής (μεταξύ των οποίων και πληρωμή μέσω κρυπτονομισμάτων).
PrivateVPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 63
- Πρωτόκολλα: OpenVPN UDP/TCP, IKEv2/IPSec, L2PT/IPSec, PPTP, SOCKS5, WireGuard
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Απόκρυψης (obfuscation), Tor μέσω VPN
- Προστασία διαρροών: DNS, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Ναι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
PrivateVPN δοκιμές ταχύτητας
Υπάρχουν πάνω από 200 διακομιστές στο παγκόσμιο δίκτυο του PrivateVPN. Δοκίμασα έναν τυχαίο διακομιστή σε καθεμία από τις 60+ χώρες του και μέτρησα την επιβράδυνση που επέφερε κάθε διακομιστής στη σύνδεσή μου. Συνδέθηκα σχεδόν άμεσα σε κάθε διακομιστή της χώρας που επιθυμούσα.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Το PrivateVPN διαθέτει πολύ καλές ταχύτητες (ειδικά το πρωτόκολλο L2PT/IPSec). Κατά τη διάρκεια των δοκιμών μου, η ταχύτητα λήψης των διακομιστών δεν έπεσε κάτω από 50% (η γενική μέτρηση για συνδέσεις υψηλής ποιότητας στο εξωτερικό). Το PrivateVPN διαθέτει το πρωτόκολλο WireGuard, ωστόσο, θα χρειαστεί να το ρυθμίσετε χειροκίνητα στη συσκευή σας. Η όλη διαδικασία μου πήρε λιγότερο από 10 λεπτά, ωστόσο, η σχετική εφαρμογή δεν χαρακτηρίζεται φιλική προς τον χρήστη, ενώ λιγότερο έμπειροι χρήστες ενδέχεται να τη βρουν έως και κακή. Για τον λόγο αυτό, προτιμώ τα VPN που περιλαμβάνουν το WireGuard ως πρωτόκολλο εντός της εφαρμογής (όπως ισχύει στα Private Internet Access και CyberGhost VPN).
- Οι δοκιμές ταχύτητας που πραγματοποίησα μαρτυρούν την ικανότητα του PrivateVPN στους τομείς του streaming, των λήψεων και των βιντεοκλήσεων. Υπήρξαν ορισμένες επιβραδύνσεις σε κοντινές συνδέσεις αλλά και σε συνδέσεις του εξωτερικού.
PrivateVPN streaming: Ισχυρό
Το PrivateVPN λειτουργεί με τα Netflix, Hulu, Amazon Prime, BBC iPlayer, Disney+ και πολλές ακόμη υπηρεσίες streaming — τα μέλη της διεθνούς μας ομάδας επιβεβαίωσαν ότι ήταν σε θέση να μεταδώσουν εκπομπές στις τοπικές βιβλιοθήκες τους ενώ ήταν συνδεδεμένοι στο VPN. Κατά τη διάρκεια των δοκιμών μου, επισκέφθηκα τα Netflix US, Amazon Prime US και Disney+ US, και χάρη στις γρήγορες ταχύτητες του PrivateVPN, η εικόνα στα βίντεό μου ήταν πάντοτε τέλεια.

PrivateVPN torrenting: Ισχυρό
Το PrivateVPN υποστηρίζει το torrenting σε κάθε διακομιστή του (όπως ισχύει και στο ExpressVPN). Δοκίμασα τυχαίους διακομιστές με κάθε κορυφαίο πρόγραμμα torrenting — uTorrent, BitTorrent, Bitport.io και πολλά ακόμη — με το PrivateVPN να τα πηγαίνει περίφημα, κατεβάζοντας και μοιράζοντας περιεχόμενο σε κάθε περίπτωση.
Επίσης, πραγματοποίησα μία σειρά από 10 δοκιμές διαρροής στο PrivateVPN μη εντοπίζοντας κάποια διαρροή DNS.
PrivateVPN gaming: Συνήθως ισχυρό
Όταν δοκίμασα το PrivateVPN με διαδικτυακά παιχνίδια όπως το Fortnite και το Counter-Strike: Global Offensive, μου παρείχε μια πολύ καλή εμπειρία multiplayer — είχα καλές τιμές ping τόσο σε τοπικούς όσο και σε απομακρυσμένους διακομιστές VPN, επομένως τα παιχνίδια μου δεν είχαν κανένα κόλλημα ή καθυστέρηση. Επιπλέον, πολύ θετικό ήταν το γεγονός πως δεν αποσυνδέθηκα ποτέ από τον gaming διακομιστή.
Όλοι οι διακομιστές του PrivateVPN διαθέτουν προστασία DDoS. Επίσης, ο πάροχος διαθέτει εύχρηστους οδηγούς εγκατάστασης που σας δείχνουν πώς να διαμορφώσετε το VPN στον δρομολογητή σας. Παρ’ όλα αυτά, αν θέλετε να χρησιμοποιήσετε το VPN στον δρομολογητή σας, ώστε να μπορείτε να παίξετε με αυτό σε συσκευές που δεν υποστηρίζουν εφαρμογές VPN (όπως οι κονσόλες Xbox και PlayStation), τότε σας προτείνω να χρησιμοποιήσετε το ExpressVPN, το οποίο διαθέτει εφαρμογή δρομολογητή που είναι πολύ απλή στην εγκατάσταση αλλά και στη χρήση.
Δυστυχώς, το PrivateVPN δεν εγγυάται ότι η υπηρεσία του θα λειτουργεί με Cloud gaming πλατφόρμες — το δοκίμασα με το Google Stadia και το GeForce Now για μία ημέρα και λειτούργησε μόνο στο 70% του χρόνου. Για να είμαι ειλικρινής, το ExpressVPN συνιστά καλύτερη επιλογή, αν ασχολείστε με το Cloud gaming, καθώς παρέχει υποστήριξη για τις πιο δημοφιλείς Cloud gaming πλατφόρμες.
PrivateVPN παράκαμψη λογοκρισίας: Ισχυρό
Το PrivateVPN διαθέτει τη λειτουργία Stealth Mode (Αόρατη Λειτουργία), η οποία ουσιαστικά αποτελεί ένα εργαλείο απόκρυψης (obfuscation) που καλύπτει την VPN κίνησή σας. Επομένως, το συγκεκριμένο VPN είναι πολύ καλό στο να παρακάμπτει τη διαδικτυακή λογοκρισία.
PrivateVPN πακέτα και τιμολόγηση
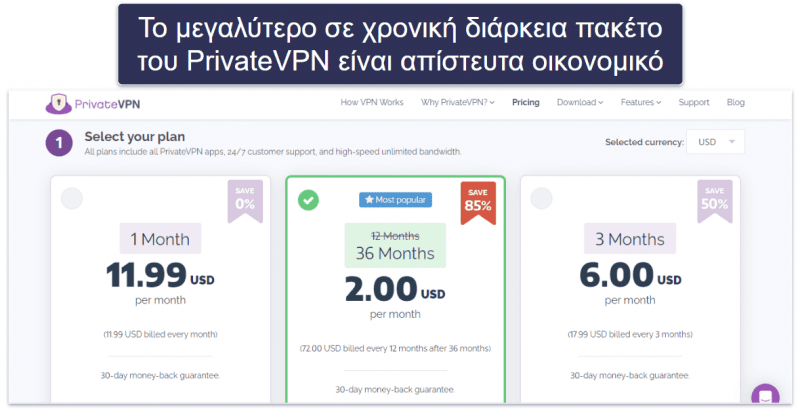
Τα μηνιαία πακέτα του PrivateVPN είναι λίγο ακριβά, ωστόσο, η πολυετή προσφορά του είναι μία από τις οικονομικότερες της λίστας — κοστίζει μόνο 2,00 $ / το μήνα, τιμή πολύ χαμηλότερη από τους περισσότερους ανταγωνιστές. Το PrivateVPN δέχεται 6 διαφορετικές πιστωτικές κάρτες (μεταξύ των οποίων τις JCB και Diner Club International), PayPal και Bitcoin. Κάθε επί πληρωμή πακέτο καλύπτεται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση τουl PrivateVPN >
7. Proton VPN — Εξαιρετικές λειτουργίες απορρήτου και γρήγορες ταχύτητες
Το Proton VPN είναι ένα ασφαλές, γρήγορο και εύχρηστο VPN, το οποίο αναπτύχθηκε από την ίδια ομάδα που δημιούργησε την κρυπτογραφημένη υπηρεσία email ProtonMail. Το Proton VPN διαθέτει μια αυστηρή πολιτική μη τήρησης αρχείων καταγραφής (ελεγμένη και επαληθευμένη), εκδίδει τακτικά αναφορές διαφάνειας για να αποδείξει ότι δεν παραδίδει δεδομένα χρήστη στις αρχές και εδρεύει στην Ελβετία (η οποία είναι εκτός δικαιοδοσίας των συμμαχιών 5/9/14 Eyes Alliance).
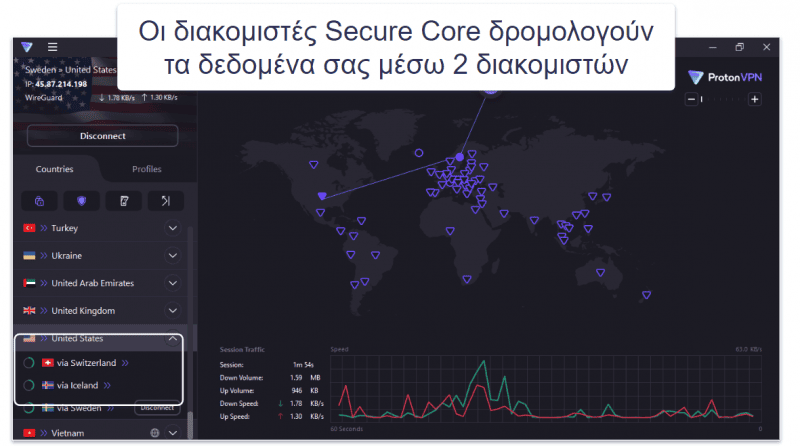
Η αρχιτεκτονική Secure Core VPN του Proton VPN μεταφέρει τη διαδικτυακή κίνηση των χρηστών μέσω πολλαπλών διακομιστών (οι οποίοι βρίσκονται σε υπόγειες αποθήκες και κέντρα δεδομένων στην Ελβετία, την Ισλανδία και τη Σουηδία),προτού τα δεδομένα εξέλθουν από το δίκτυο του Proton VPN.
Μάλιστα, όλες οι εφαρμογές του Proton VPN είναι ανοιχτού κώδικα, επιτρέποντας σε οποιονδήποτε να εξετάσει τον πηγαίο κώδικα του λογισμικού και να αναζητήσει τρύπες στην ασφάλεια ή το απόρρητό του (οι εφαρμογές έχουν ελεγχθεί και επαληθευτεί από ανεξάρτητους φορείς). Επιπλέον, οι macOS και iOS εφαρμογές του Proton VPN υποστηρίζουν Ελληνικά.
Το Proton VPN διαθέτει πλήρη κρυπτογράφηση δίσκου (κρυπτογραφεί όλα τα δεδομένα σε έναν διακομιστή, ώστε να είναι αδύνατο να αναγνωστούν) και μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy). Επίσης, προσφέρει πρόσθετες λειτουργίες όπως διαχωρισμό σήραγγας, πρόγραμμα αποκλεισμού διαφημίσεων, ιχνηλατών και κακόβουλου λογισμικού, ενώ λειτουργεί με μεγάλες υπηρεσίες streaming και υποστηρίζει το torrenting. Ακόμη, το Proton VPN παρέχει πρόσβαση στο Tor μέσω συνδέσεων VPN, επιτρέποντάς σας την περιήγηση σε ιστότοπους .onion από τον κανονικό/συνηθισμένο περιηγητή σας, ενώ παράλληλα διατηρείτε τη διεύθυνση IP σας κρυμμένη από οποιονδήποτε κόμβο του Tor.
Η μητρική εταιρεία του Proton VPN ανέπτυξε επίσης το Proton Pass, έναν πολύ καλό διαχειριστή κωδικών πρόσβασης. Διαθέτει βασικές λειτουργίες, όπως αυτόματη συμπλήρωση, κρυπτογράφηση από άκρο σε άκρο και γεννήτρια κωδικών πρόσβασης. Επίσης, παρέχει χρήσιμα πρόσθετα, όπως ψευδώνυμα email, τα οποία σας βοηθούν να αποτρέψετε την αποκάλυψη ή διαρροή της πραγματικής σας διεύθυνσης email. Τέλος, το Proton Pass διαθέτει μία δωρεάν και μία επί πληρωμή έκδοση.
Το Proton VPN προσφέρει μια ικανοποιητική δωρεάν έκδοση καθώς και πολλά επί πληρωμή πακέτα, τα οποία καλύπτονται με μία αναλογική εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών (αναλογικά σημαίνει ότι θα χρεωθείτε για κάθε ημέρα χρήσης της υπηρεσίας μέχρι την προθεσμία των 30 ημερών).
Proton VPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 112
- Πρωτόκολλα: OpenVPN, IKEv2/IPSec, WireGuard, Stealth
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Secure Core, P2P, Streaming, Tor μέσω VPN, διαχωρισμού σήραγγας
- Προστασία διαρροών: DNS, WebRTC, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Όχι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
Proton VPN δοκιμές ταχύτητας
Δοκίμασα έναν τυχαίο διακομιστή σε καθεμία από τις 68 χώρες του Proton VPN, ώστε να το συγκρίνω με τους ανταγωνιστές του.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Οι ταχύτητες του Proton VPN ήταν αρκετά γρήγορες στις δοκιμές ταχύτητας που πραγματοποίησα. Αν και μείωσε τις ταχύτητες λήψης κατά μέσο όρο 24% (λίγο πιο αργό από το ExpressVPN), ήμουν σε θέση να περιηγηθώ απρόσκοπτα στο διαδίκτυο, να μεταδώσω βίντεο και να πραγματοποιήσω κλήσεις VoIP (Voice over Internet Protocol) ακόμα και όταν ήμουν συνδεδεμένος σε κάποιον απομακρυσμένο διακομιστή. Επίσης, το Proton VPN διαθέτει τη λειτουργία VPN Accelerator (Επιταχυντής VPN), η οποία χρησιμοποιεί εργαλεία υψηλής τεχνολογίας για τη μείωση του λανθάνοντος χρόνου και την αύξηση των ταχυτήτων, ιδίως σε απομακρυσμένους διακομιστές (οι ταχύτητες μου αυξήθηκαν έως και 40% σε ορισμένους διακομιστές).
Proton VPN streaming: Ισχυρό
Το Proton VPN λειτουργεί με 30+ υπηρεσίες streaming, εκ των οποίων αρκετές δημοφιλείς, όπως είναι τα Netflix, Hulu και Max, αλλά και ορισμένες λιγότερο γνωστές πλατφόρμες, όπως είναι τα Peacock και Pluto TV — όπως επιβεβαιώθηκε από τους συναδέλφους μου που βρίσκονται σε ολόκληρο τον κόσμο. Στις δοκιμές μου, λειτούργησε με τα Netflix US, Hulu, Amazon Prime US, ενώ ο συνάδελφός μου από το Ηνωμένο Βασίλειο με ενημέρωσε ότι λειτούργησε με τα Netflix UK, Amazon Prime UK και BBC iPlayer.

Proton VPN torrenting: Συνήθως ισχυρό
Το Proton VPN υποστηρίζει το torrenting μόνο σε αποκλειστικούς/ειδικούς διακομιστές P2P — διαθέτει 300+ διακομιστές P2P που βρίσκονται σε 20+ χώρες, συμπεριλαμβανομένης της Βόρειας Αμερικής, της Ευρώπης, της Ισλανδίας, του Χονγκ Κονγκ, της Νιγηρίας και της Σιγκαπούρης (υπάρχουν 140+ στις ΗΠΑ). Το Proton VPN θα σας ανακατευθύνει αυτόματα σε έναν από τους αποκλειστικούς διακομιστές P2P του, αν αναγνωρίσει κίνηση P2P. Ωστόσο, προτιμώ τα VPN που επιτρέπουν το torrenting σε κάθε τους διακομιστή, όπως συμβαίνει στα ExpressVPN και Private Internet Access.
Πραγματοποίησα δοκιμές διαρροής DNS σε κάθε διακομιστή P2P του Proton VPN — όπου εντοπίστηκαν 0 διαρροές DNS.
Proton VPN gaming: Ισχυρό
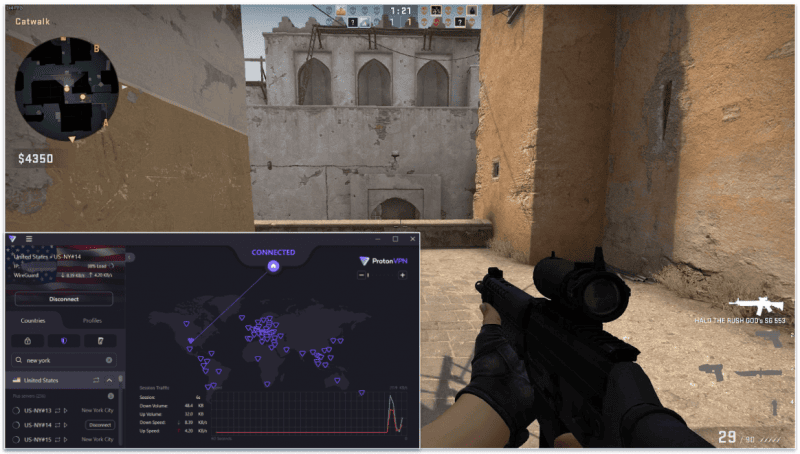
Το Proton VPN είναι πολύ καλό για gaming — είχα πολύ χαμηλό ping και γρήγορες συνδέσεις όσο ήμουν συνδεδεμένος σε έναν τοπικό διακομιστή. Το ping μου ήταν πολύ υψηλότερο όταν συνδέθηκα σε έναν απομακρυσμένο διακομιστή, όπου αντιμετώπισα ορισμένες επιβραδύνσεις, χωρίς αυτές να είναι κάτι το σημαντικό. Έτσι, ήμουν σε θέση να απολαύσω την gaming συνεδρία μου. Επιπλέον, οι συνδέσεις μου με τον gaming διακομιστή δεν διακόπηκαν ποτέ.
Όλοι οι διακομιστές του Proton VPN διαθέτουν προστασία DDoS. Επιπλέον, μπορείτε να ρυθμίσετε το Proton VPN στο δρομολογητή σας χειροκίνητα. Ο πάροχος διαθέτει πολλές χρήσιμες οδηγίες (περιλαμβάνονται ακόμη και στιγμιότυπα οθόνης) — ωστόσο, σε περίπτωση που επιθυμείτε να παίξετε μέσω μίας συσκευής που δεν υποστηρίζει εφαρμογές VPN, το ExpressVPN αποτελεί καλύτερη επιλογή, καθώς συνοδεύεται από μια εφαρμογή δρομολογητή που είναι εύκολη στην εγκατάσταση και στη χρήση (επιπλέον, το εν λόγω VPN διαθέτει δικό του δρομολογητή).
Όταν μίλησα με τους αντιπροσώπους του τμήματος υποστήριξης του Proton VPN σχετικά με το θέμα της υποστήριξης του gaming στο Cloud, αυτοί μου επισήμαναν πως δεν μπορούν να εγγυηθούν ότι το Proton VPN θα λειτουργήσει με υπηρεσίες όπως το PlayStation Now και το GeForce Now. Στις δοκιμές μου, λειτούργησε χωρίς προβλήματα, αλλά μπορεί να μη συμβεί το ίδιο και σε εσάς — αν χρειάζεστε ένα πραγματικά καλό VPN για gaming στο Cloud, ρίξτε μια ματιά στο ExpressVPN, το οποίο λειτουργεί με 5+ δημοφιλείς Cloud gaming πλατφόρμες.
Proton VPN παράκαμψη λογοκρισίας: Αδύναμο
Δυστυχώς, το Proton VPN δεν λειτουργεί στην Κίνα και ενδεχομένως να λειτουργεί μόνο σε άλλες χώρες που υπόκεινται σε περιορισμούς — παρά το γεγονός ότι το VPN παρέχει πρόσβαση σε λειτουργίες απόκρυψης (obfuscation). Ως συνέπεια, το εν λόγω VPN δεν αποτελεί καλή επιλογή σε περίπτωση που αναζητείτε ελεύθερη πρόσβαση στο διαδίκτυο από μία χώρα με περιορισμούς.
Proton VPN πακέτα και τιμολόγηση

Η δωρεάν έκδοση του Proton VPN είναι αρκετά καλή, προσφέροντας απεριόριστα δεδομένα. Παρ’ όλα αυτά, φέρει και ορισμένους περιορισμούς — μπορείτε να συνδέσετε μόνο 1 συσκευή ενώ μπορείτε να αποκτήσετε πρόσβαση μόνο σε διακομιστές από 5 χώρες (στην Πολωνία, τη Ρουμανία, την Ολλανδία, την Ιαπωνία και τις ΗΠΑ, όπου συμπεριλαμβάνονται η Νέα Υόρκη, το Μαϊάμι και το Λος Άντζελες).
Το Proton VPN διαθέτει premium πακέτα διάρκειας 1 μήνα, 1 έτους και 2 ετών. Τα πακέτα διάρκειας 1 έτους και 2 ετών είναι ακριβότερα από τα αντίστοιχα μακροπρόθεσμα πακέτα άλλων κορυφαίων VPN, αλλά και πάλι αξίζουν — προτείνω το μεγαλύτερο σε διάρκεια πακέτο, το οποίο ξεκινά από τα 3,59 $ / το μήνα, γιατί είναι το πιο συμφέρον από οικονομικής άποψης.
Διαβάστε την πλήρη αξιολόγηση του Proton VPN >
8. TunnelBear — Καλό VPN για αρχάριους
Το TunnelBear είναι ένα από τα πιο ευκολονόητα VPN στην αγορά — είναι πολύ εύκολο στη χρήση (ακόμα κι αν δεν έχετε χρησιμοποιήσει ποτέ ξανά VPN) διαθέτοντας έναν πολύ χαριτωμένο σχεδιασμό (υπάρχουν χαριτωμένες αρκούδες σε όλη την εφαρμογή).
Επίσης, το TunnelBear είναι πολύ ασφαλές, προσφέρει ικανοποιητικές ταχύτητες, επιτρέπει απεριόριστες συνδέσεις και διαθέτει όλα τα βασικά χαρακτηριστικά ασφαλείας ενός VPN, συμπεριλαμβανομένης μιας αυστηρής πολιτικής μη καταγραφής που ελέγχεται και επαληθεύεται ετησίως από μια ανεξάρτητη εταιρεία ασφάλειας στον κυβερνοχώρο. Επιπλέον, το TunnelBear διαθέτει διακόπτη έκτακτης ανάγκης, λειτουργία απόκρυψης (obfuscation) και διαχωρισμό σήραγγας για Android (σας επιτρέπει να εξαιρέσετε εφαρμογές) — και είναι το μοναδικό VPN σε αυτήν τη λίστα που διαθέτει διαχωρισμό σήραγγας στο iOS (σας επιτρέπει να εξαιρέσετε ιστότοπους, ακόμη και υποτομείς). Ακόμη, συνοδεύεται από ένα δωρεάν πρόγραμμα αποκλεισμού διαφημίσεων (μόνο για Chrome). Ωστόσο, σε αντίθεση με άλλους κορυφαίους ανταγωνιστές, όπως είναι τα ExpressVPN και CyberGhost VPN, το TunnelBear δεν λειτουργεί σταθερά με δημοφιλείς υπηρεσίες streaming.
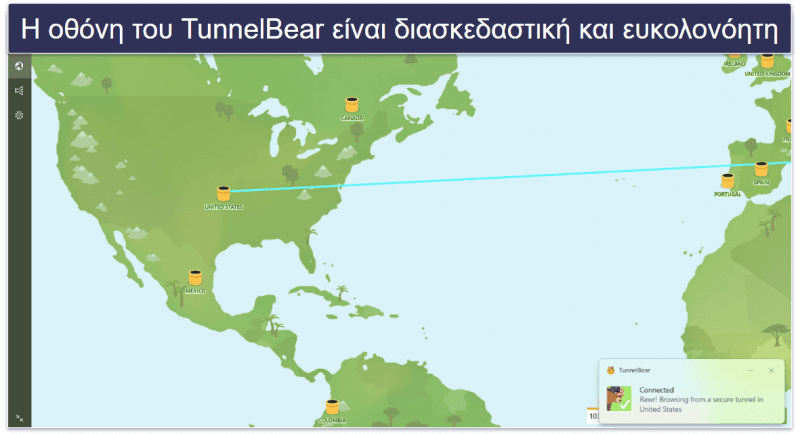
Ωστόσο, σε αντίθεση με άλλους κορυφαίους ανταγωνιστές, όπως το ExpressVPN και το CyberGhost VPN, το TunnelBear δεν λειτουργεί πάντοτε με όλες τις δημοφιλείς υπηρεσίες streaming.
Το TunnelBear προσφέρει απεριόριστες συνδέσεις, αλλά είναι απογοητευτικό που δεν προσφέρει εγγύηση επιστροφής χρημάτων. Ωστόσο, αν σας ενδιαφέρει, μπορείτε να δοκιμάσετε το TunnelBear μέσω του δωρεάν πακέτου του (το οποίο διαθέτει μόνο 2 GB ανά μήνα).
TunnelBear στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 47
- Πρωτόκολλα: OpenVPN, IKEv2, WireGuard
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Διαχωρισμού σήραγγας, απόκρυψης (obfuscation)
- Προστασία διαρροών: DNS, WebRTC, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Μη διαθέσιμο
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Μη διαθέσιμο
TunnelBear δοκιμές ταχύτητας
Το TunnelBear διαθέτει διακομιστές μόνο σε 47 χώρες — λιγότερους από πολλούς premium ανταγωνιστές, όπως τα ExpressVPN, Private Internet Access και CyberGhost VPN. Ωστόσο, οι διακομιστές του TunnelBear είναι καλά κατανεμημένοι ανά τον κόσμο (Βόρεια, Κεντρική και Νότια Αμερική, Ευρώπη, Αυστραλία, Σιγκαπούρη, Ιαπωνία, Νέα Ζηλανδία). Συνδέθηκα σε έναν διακομιστή σε κάθε χώρα για να δοκιμάσω την ταχύτητα του TunnelBear.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Συνολικά, το TunnelBear μείωσε την ταχύτητα λήψης μου κατά μέσο όρο 42%, τιμή αρκετά καλή — αλλά χειρότερη από το ExpressVPN και το Private Internet Access. Όταν συνδέθηκα σε έναν τοπικό διακομιστή (Η.Π.Α.), η ταχύτητα περιήγησής μου παρέμεινε σχεδόν ίδια με αυτήν που είχα χωρίς τη χρήση VPN, ενώ ήμουν σε θέση να μεταδώσω βίντεο χωρίς καθυστέρηση (μάλιστα, η ταχύτητα μεταφόρτωσης αυξήθηκε!). Επίσης, όταν συνδέθηκα σε έναν διακομιστή στη Γερμανία και στο Ηνωμένο Βασίλειο, περιηγήθηκα στο διαδίκτυο, μετέδωσα περιεχόμενο και κατέβασα αρχεία χωρίς κανένα απολύτως πρόβλημα. Ωστόσο, οι ταχύτητες λήψης και μεταφόρτωσης μειώθηκαν σημαντικά μόλις συνδέθηκα σε απομακρυσμένους διακομιστές στην Ιαπωνία, στην Ινδία και στην Αυστραλία — χρειάστηκαν έως και 7 δευτερόλεπτα για να φορτωθούν οι ιστότοποι, ενώ το streaming περιεχόμενο φόρτωνε για περίπου 10 δευτερόλεπτα προτού ξεκινήσει να παίζει.
TunnelBear streaming: Συνήθως ισχυρό
Το TunnelBear είναι μια τίμια επιλογή για streaming. Στις δοκιμές μου, το TunnelBear λειτούργησε με τα Netflix US, Amazon Prime US και Hulu, καθώς και με λιγότερο γνωστούς ιστότοπους, όπως τα Pluto TV και Crunchyroll. Δυστυχώς, το TunnelBear δεν λειτουργεί με τα Disney+ και ESPN+.

TunnelBear torrenting: Ισχυρό
Όπως το ExpressVPN, έτσι και το TunnelBear επιτρέπει την κοινή χρήση P2P σε όλους τους διακομιστές του. Ωστόσο, επειδή δεν διαθέτει τις υψηλότερες ταχύτητες, σας συνιστώ να συνδεθείτε σε έναν διακομιστή χρησιμοποιώντας την επιλογή Fastest Connection (Ταχύτερη σύνδεση) ή να επιλέξετε χειροκίνητα έναν διακομιστή που βρίσκεται στην κοντινότερη χώρα.
TunnelBear gaming: Συνήθως αδύναμο
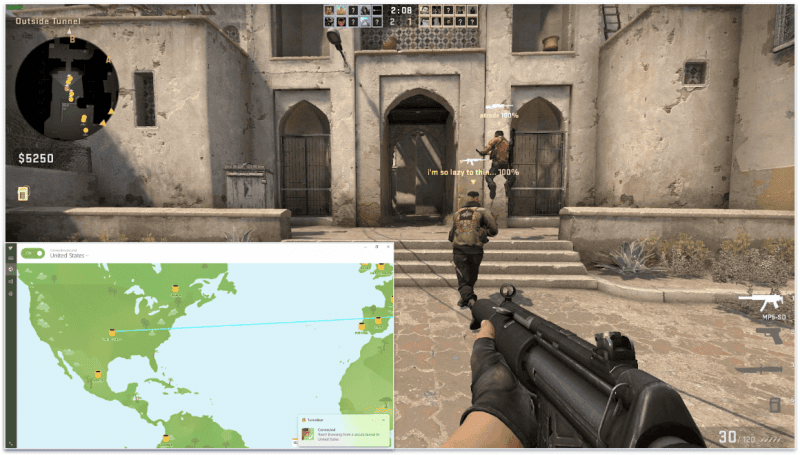
Το TunnelBear είναι ικανοποιητικό για gaming, αφού μου παρείχε καλό ping ενώ ήμουν συνδεδεμένος σε τοπικούς αλλά και απομακρυσμένους διακομιστές. Αντιμετώπισα κάποια καθυστέρηση, αλλά αυτή δεν ήταν πολύ αισθητή — επιπλέον, μου άρεσε που οι συνδέσεις μου με τους gaming διακομιστές δεν διακόπηκαν ποτέ. Ωστόσο, αν ψάχνετε για ένα gaming VPN χωρίς επιβραδύνσεις, σας προτείνω να κοιτάξετε τα ExpressVPN, Private Internet Access και CyberGhost VPN.
Αν και είναι πολύ θετικό που το TunnelBear διαθέτει προστασία DDoS στους διακομιστές του, είναι κρίμα που δεν προσφέρει υποστήριξη για δρομολογητές (όπως συμβαίνει στα ExpressVPN, Private Internet Access και NordVPN) — επομένως δεν μπορείτε να χρησιμοποιήσετε το TunnelBear για να παίξετε παιχνίδια σε συσκευές που δεν υποστηρίζουν εγγενώς VPN, όπως για παράδειγμα σε μια κονσόλα Xbox ή στο Nintendo Switch. Αν το παραπάνω αποτελεί καθοριστικό παράγοντα για εσάς και θέλετε να επιλέξετε ένα διαφορετικό VPN, σας προτείνω το ExpressVPN, το οποίο διαθέτει αποκλειστική εφαρμογή δρομολογητή.
Οι αντιπρόσωποι του TunnelBear μου ανέφεραν ότι η υπηρεσία τους ενδέχεται να λειτουργεί με Cloud gaming πλατφόρμες, ωστόσο, δεν μπορούν να το εγγυηθούν. Όταν χρησιμοποίησα το TunnelBear με διάφορες Cloud gaming υπηρεσίες, αυτό λειτούργησε — αλλά μόνο στο 60% των περιπτώσεων. Αν θέλετε ένα Cloud gaming VPN, τότε πιστεύω ότι πρέπει να επιλέξετε το ExpressVPN, το οποίο λειτουργεί σταθερά με κάθε δημοφιλή Cloud gaming πλατφόρμα.
TunnelBear παράκαμψη λογοκρισίας: Ισχυρό
Το TunnelBear διαθέτει ένα εργαλείο απόκρυψης (obfuscation), το GhostBear, το οποίο μπορείτε να ενεργοποιήσετε με ένα μόνο κλικ. Όπως συμβαίνει στα ExpressVPN και Private Internet Access, το εργαλείο απόκρυψης του TunnelBear ξεπερνά επιτυχώς τους διαδικτυακούς περιορισμούς και τους αποκλεισμούς VPN.
TunnelBear πακέτα και τιμολόγηση

Σε αντίθεση με το Proton VPN, το οποίο παρέχει απεριόριστα δεδομένα στους δωρεάν χρήστες, το δωρεάν πακέτο του TunnelBear περιλαμβάνει μόνο 2 GB ανά μήνα — το οποίο επαρκεί απλά για να δοκιμάσετε την ταχύτητα περιήγησης του TunnelBear (δεν αρκεί streaming ή torrenting).
Το επί πληρωμή πακέτο Unlimited περιλαμβάνει 3 ετήσιες επιλογές συνδρομής, ενώ όλα τα πακέτα επιτρέπουν απεριόριστο αριθμό ταυτόχρονων συνδέσεων. Με τιμή εκκίνησης τα 3,33 $ / το μήνα, τα premium πακέτα του TunnelBear είναι λίγο ακριβότερα από ορισμένους ανταγωνιστές — αν και αξίζουν πραγματικά, σε περίπτωση που ψάχνετε ένα απλό και εύχρηστο VPN (επιπλέον, έχει χαριτωμένες αρκούδες σε κάθε του εφαρμογή).
Το TunnelBear δέχεται πιστωτικές κάρτες και Bitcoin (όχι PayPal), ενώ σύμφωνα με τον ιστότοπο της εταιρείας, μπορείτε να πληρώσετε ακόμη και με βάζα μέλι (το οποίο δεν δοκίμασα!). Το TunnelBear δεν διαθέτει εγγύηση επιστροφής χρημάτων.
Διαβάστε την πλήρη αξιολόγηση του TunnelBear >
9. VyprVPN — Καλό για να παρακάμψετε τους περιορισμούς του διαδικτύου (+ κορυφαία επιλογή για μικρές επιχειρήσεις)
Το VyprVPN ανταποκρίνεται εξαιρετικά σε περιοχές με περιορισμούς (λογοκρισία, τείχη προστασίας) — λειτουργεί με 45+ υπηρεσίες streaming, συμπεριλαμβάνοντας τις πιο δημοφιλείς, όπως είναι τα Netflix και Amazon Prime. Στις δοκιμές μου, το περιεχόμενο ροής ξεκίνησε αμέσως, σχεδόν χωρίς κανένα φαινόμενο buffering (ακόμα και σε πολύ απομακρυσμένους διακομιστές).
Το VyprVPN διαθέτει το δικό του ιδιόκτητο πρωτόκολλο Chameleon για την παράκαμψη των αποκλεισμών VPN — το εν λόγω πρωτόκολλο χρησιμοποιεί μηχανισμό απόκρυψης (obfuscation), ώστε να αποκρύψει την VPN κίνησή σας και να σας επιτρέψει να σερφάρετε στο διαδίκτυο χωρίς περιορισμούς.
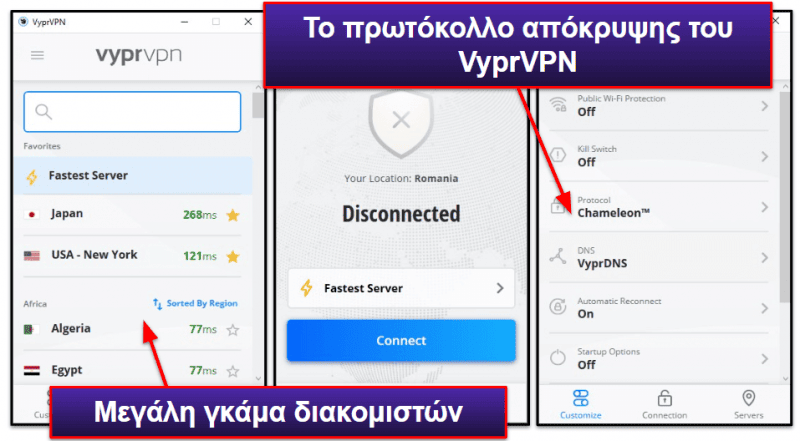
Επίσης, αποτελεί μια πολύ καλή επιλογή για επαγγελματίες χρήστες — έχει υπό την κατοχή και τη λειτουργία του όλους τους διακομιστές του, εδρεύει στην Ελβετία (χώρα με αυστηρούς νόμους περί απορρήτου) και δεν διατηρεί αρχεία καταγραφής δραστηριότητας στο διαδίκτυο ή αρχεία, τα οποία μοιράζεστε εσείς ή οι υπάλληλοί σας.
Το VyprVPN επιτρέπει έως και 10 συνδέσεις, διαθέτει μηνιαία και ετήσια πακέτα, ενώ συνοδεύεται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
VyprVPN στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 64
- Πρωτόκολλα: WireGuard, IKEv2/IPSec, OpenVPN, Chameleon (απόκρυψη-obfuscation)
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Διαχωρισμού σήραγγας
- Προστασία διαρροών: DNS
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Μη διαθέσιμο
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
VyprVPN δοκιμές ταχύτητας
Το VyprVPN διαθέτει διακομιστές σε 64 χώρες σε ολόκληρο τον κόσμο. Δοκίμασα την ταχύτητα του VyprVPN επιλέγοντας έναν διακομιστή σε καθεμία από τις τοποθεσίες του VyprVPN.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Το VyprVPN μου παρείχε εξαιρετικές ταχύτητες κατά τη σύνδεσή μου σε διακομιστές στις ΗΠΑ και στην Ευρώπη αλλά ακόμη και σε μακρινές τοποθεσίες, όπως η Ιαπωνία και η Αυστραλία. Ωστόσο, η ταχύτητα του VyprVPN μειώθηκε περισσότερο απ’ όσο θα ήθελα, όταν συνδέθηκα σε διακομιστές στην Ασία και τη Νότια Αμερική. Παρ’ όλα αυτά, γενικά η μέση μείωση της ταχύτητάς μου ανήλθε στο 21%, τιμή αρκετά καλή.
VyprVPN streaming: Ισχυρό
Το VyprVPN λειτουργεί με τα Netflix, Hulu, Amazon Prime, AppleTV, BBC iPlayer και ESPN+. Αλλά αν είστε μεγάλος θαυμαστής των τίτλων της Disney και της Marvel, θα απογοητευτείτε όταν μάθετε ότι το VyprVPN δεν λειτουργεί με το Disney+. Για να επισκεφθείτε το Disney+, σας προτείνω να χρησιμοποιήσετε άλλα κορυφαία VPN, όπως τα ExpressVPN, Private Internet Access και CyberGhost VPN.
Κατά τη διάρκεια των δοκιμών μου, μπόρεσα να επισκεφθώ όλες τις υπηρεσίες streaming, που είναι διαθέσιμες στις ΗΠΑ, και χάρη στις γρήγορες ταχύτητες του VyprVPN δεν αντιμετώπισα διακοπές στα βίντεό μου σε HD ποιότητα.

VyprVPN torrenting: Ισχυρό
Το VyprVPN αποτελεί μια υπηρεσία φιλική προς to torrenting, η οποία επιτρέπει την κοινή χρήση αρχείων P2P σε όλους τους διακομιστές της. Απόλαυσα γρήγορες ταχύτητες καθώς και μια γρήγορη και απρόσκοπτη εμπειρία torrenting κατά τη διάρκεια των δοκιμών μου. Μάλιστα, το VyprVPN πέρασε επιτυχώς κάθε δοκιμή διαρροής DNS που διενήργησα (0 διαρροές).
VyprVPN gaming: Συνήθως ισχυρό
Το VyprVPN είναι ένα από τα καλύτερα gaming VPN στην αγορά — παρέχει σταθερά καλές τιμές ping τόσο σε τοπικούς όσο και σε απομακρυσμένους διακομιστές, διαθέτοντας πολύ γρήγορες ταχύτητες λήψης (μου πήρε μόνο περίπου 20–22 λεπτά για να κατεβάσω το Dota 2, μεγέθους περίπου 35 GB δεδομένων). Επιπλέον, για όση ώρα έπαιζα με το VyprVPN, δεν αντιμετώπισα ποτέ καθυστερήσεις ή διακοπές σύνδεσης. Το VyprVPN παρέχει προστασία DDoS σε κάθε διακομιστή του διαθέτοντας και υποστήριξη δρομολογητή.
Σε ό,τι αφορά το Cloug gaming το VyprVPN δεν αναφέρει ότι διαθέτει σχετική υποστήριξη — ήρθα σε επικοινωνία με το τμήμα εξυπηρέτησης πελατών, όπου οι αντιπρόσωποι μου ανέφεραν ότι δεν μπορούν να εγγυηθούν τη λειτουργία του VyprVPN σε πλατφόρμες όπως τα Google Stadia και GeForce Now. Στις δοκιμές που πραγματοποίησα, το VyprVPN λειτούργησε καλά, αλλά τα αποτελέσματα ενδεχομένως να μην είναι τα ίδια για εσάς. Σε κάθε περίπτωση, αν χρειάζεστε κυρίως ένα VPN για Cloud Gaming, τότε θα σας πρότεινα το ExpressVPN, το οποίο είναι συμβατό με 5+ κορυφαίες Cloud gaming.
VyprVPN παράκαμψη λογοκρισίας: Ισχυρό
Το VyprVPN διαθέτει ένα ειδικό πρωτόκολλο που ονομάζεται Chameleon, το οποίο διατηρεί τη VPN κίνησή σας μη ανιχνεύσιμη. Επίσης, το Chameleon ανανεώνει τακτικά τη διεύθυνση IP σας κατά τη διάρκεια της σύνδεσης VPN, ώστε να προστατεύσει καλύτερα το απόρρητό σας και να σας θωρακίσει απέναντι στους αποκλεισμούς IP.
VyprVPN πακέτα και τιμολόγηση
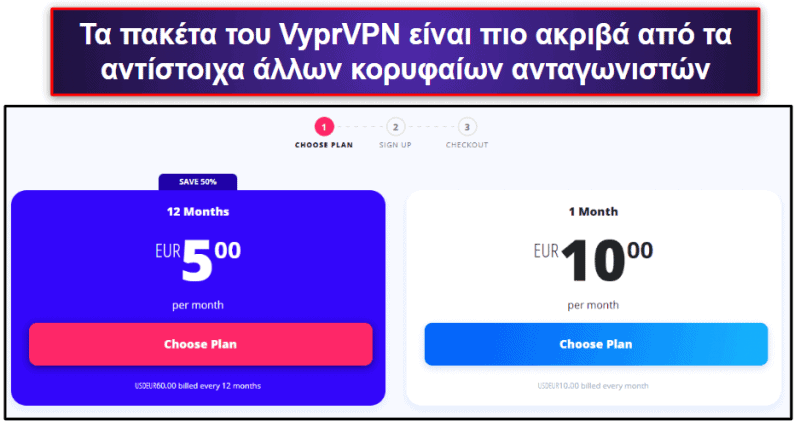
Το VyprVPN προσφέρει διάφορα πακέτα, με τις τιμές να ξεκινούν από τα 3,00 $ / το μήνα. Μπορείτε να πληρώσετε με πιστωτική κάρτα, UnionPay, Amazon Pay και PayPal (αλλά όχι με κρυπτονομίσματα). Μάλιστα, κάθε πακέτο περιλαμβάνει εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Το VyprVPN διαθέτει τα πακέτα VyprVPN for Business και VyprVPN for Business Cloud για επιχειρήσεις. Και τα δύο επιχειρηματικά πακέτα συνοδεύονται από μία δωρεάν δοκιμή.
Διαβάστε την πλήρη αξιολόγηση του VyprVPN >
10. IPVanish — Καλό για torrenting
Το IPVanish είναι πολύ καλό για torrenting. Μου αρέσει ιδιαίτερα που όλοι οι διακομιστές του υποστηρίζουν κίνηση P2P και ότι λειτουργεί με κορυφαίες εφαρμογές torrenting, όπως είναι τα uTorrent και Vuze. Επίσης, το IPVanish διαθέτει 20+ διακομιστές SOCKS5, οι οποίοι παρέχουν ταχύτερες λήψεις σε σύγκριση με τους διακομιστές VPN μιας και δεν χρησιμοποιούν κρυπτογράφηση (αλλά εξακολουθούν να αλλάζουν τη διεύθυνση IP σας).
Επιπλέον, ο πάροχος διαθέτει φιλικές προς τον χρήστη εφαρμογές για κάθε κορυφαία πλατφόρμα. Ακόμη, μου αρέσει που το συγκεκριμένο VPN υποστηρίζει απεριόριστες συνδέσεις.
Επιπροσθέτως, το IPVanish παρέχει εξίσου καλή ασφάλεια, περιλαμβάνοντας προηγμένα χαρακτηριστικά ασφαλείας, όπως είναι ο μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy). Τέλος, οι εφαρμογές του είναι εύκολες στην εγκατάσταση και διαθέτουν ευκολονόητο σχεδιασμό.
Ωστόσο, σε αντίθεση με άλλους ανταγωνιστές, όπως είναι τα ExpressVPN, Private Internet Access και CyberGhost VPN, το IPVanish δεν είναι τόσο καλό για streaming.
Το IPVanish προσφέρει μηνιαία και ετήσια πακέτα που υποστηρίζονται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
IPVanish στοιχεία περί ασφάλειας
- Αριθμός χωρών με διακομιστή: 56
- Πρωτόκολλα: WireGuard, IKEv2, OpenVPN και IPSec
- Κρυπτογράφηση δεδομένων: 256-bit AES
- Εξειδικευμένοι διακομιστές: Διαχωρισμού σήραγγας, SOCKS5
- Προστασία διαρροών: DNS, IPv6
- Διακόπτης έκτακτης ανάγκης: Ναι
- Πολιτική μη τήρησης αρχείων καταγραφής: Ναι
- Διακομιστές αποκλειστικής τεχνολογίας RAM: Όχι
- Μηχανισμός κρυπτογράφησης PFS (Perfect Forward Secrecy): Ναι
IPVanish δοκιμές ταχύτητας
Το IPVanish διαθέτει περισσότερους από 2,400+ διακομιστές σε 52 χώρες. Μου αρέσει που το IPVanish σας παρέχει διαφόρων ειδών μετρήσεις, όπως είναι το φορτίο και το ping κάθε διακομιστή, οι οποίες διευκολύνουν τις διαδικασίες εύρεσης των ταχύτερων διακομιστών.
Για τον έλεγχο των ταχυτήτων του IPVanish, συνδέθηκα σε έναν διακομιστή με το χαμηλότερο φορτίο σε καθεμία από τις 50+ χώρες.
Ορίστε μερικά από τα βασικότερα στοιχεία:
Το IPVanish με συνέδεσε σχεδόν άμεσα σε κάθε διακομιστή, ενώ διατήρησα ταχύτητες πάνω από το μέσο όρο καθ’ όλη τη διάρκεια των δοκιμών μου.
Γενικότερα, η ταχύτητά μου μειώθηκε κατά μέσο όρο περίπου 33% — τιμή συγκρίσιμη με αυτή άλλων κορυφαίων ανταγωνιστών, όπως είναι το CyberGhost. Επομένως, αν ψάχνετε για ένα VPN με καλές ταχύτητες, το IPVanish αποτελεί μια αρκετά αξιόλογη επιλογή.
Παρ’ όλα αυτά, δυσαρεστήθηκα από το γεγονός ότι χρειάστηκα περίπου 10 με 30 δευτερόλεπτα για κάθε μου σύνδεση σε έναν διακομιστή VPN — σε κορυφαία VPN, όπως είναι το ExpressVPN, δεν χρειάστηκα ποτέ περισσότερο από 5 δευτερόλεπτα για να συνδεθώ σε έναν διακομιστή VPN.
IPVanish streaming: Συνήθως αδύναμο
Το IPVanish λειτούργησε με το Netflix US αλλά όχι με το Hulu, την τοπική μου βιβλιοθήκη στο Disney+, καθώς και με άλλους ιστότοπους streaming που δοκίμασα. Υπάρχουν πολλά άλλα VPN σε αυτήν τη λίστα (όπως είναι τα ExpressVPN, Private Internet Access και CyberGhost VPN) που είναι πολύ καλύτερα για streaming.
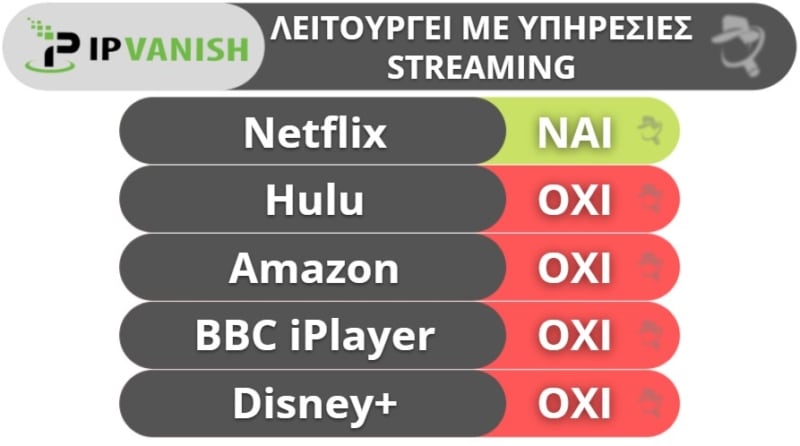
IPVanish torrenting: Ισχυρό
Και οι 2,400+ του IPVanish υποστηρίζουν κίνηση P2P, ενώ διατίθενται διακομιστές μεσολάβησης SOCKS5 που παρέχουν ακόμη γρηγορότερες λήψεις από τη στιγμή που δεν κρυπτογραφούν τα δεδομένα σας — πραγματοποίησα σχετικές δοκιμές όπου συνήθως είχα 10% υψηλότερες ταχύτητες λήψης κατά τη χρήση των διακομιστών μεσολάβησης SOCKS5.
IPVanish gaming: Ισχυρό
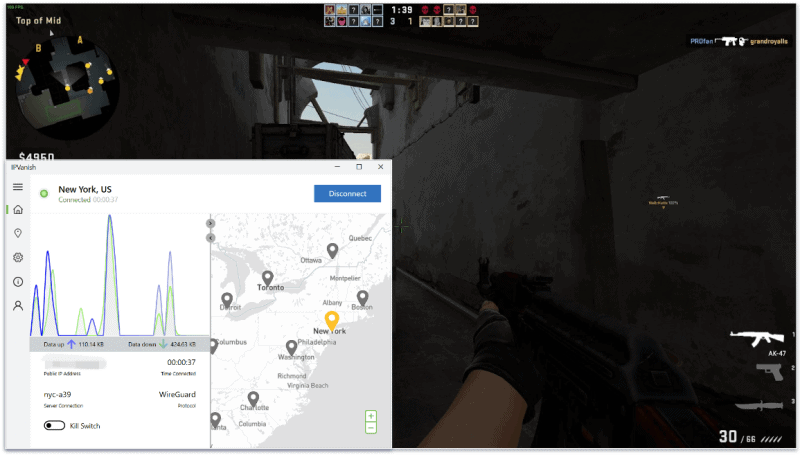
Το IPVanish είναι εξαιρετικό για gaming. Πέρασα μερικές ώρες παίζοντας Fortnite και Dota 2 χρησιμοποιώντας τοπικούς αλλά και απομακρυσμένους διακομιστές, διατηρώντας κάθε φορά καλές τιμές ping — έτσι, δεν αντιμετώπισα ποτέ κολλήματα, παγώματα, επιβραδύνσεις ή διακοπές συνδέσεων κατά τη διάρκεια του παιχνιδιού.
Με το IPVanish, λαμβάνετε προστασία DDoS σε όλους τους διακομιστές, ενώ μπορείτε να ρυθμίσετε χειροκίνητα το VPN στον δρομολογητή σας, ώστε να το χρησιμοποιήσετε καθώς παίζετε στο PlayStation ή στο Nintendo Switch — αν και το IPVanish διαθέτει χρήσιμους οδηγούς εγκατάστασης που περιλαμβάνουν στιγμιότυπα οθόνης, συνεχίζω να θεωρώ τη χρήση της εφαρμογής δρομολογητή του ExpressVPN πολύ πιο εύκολη τόσο από πλευράς ρύθμισης όσο και από πλευράς χρήσης (η διεπαφή του μοιάζει πολύ με όλες τις άλλες εφαρμογές του ExpressVPN).
Επίσης, μου αρέσει που το IPVanish υποστηρίζει το Cloud gaming, όπως ισχύει και στο ExpressVPN — δεν αντιμετώπισα κανένα πρόβλημα με το εν λόγω VPN κατά τη διάρκεια των παιχνιδιών σε gaming πλατφόρμες, όπως τα Google Stadia και GeForce Now.
IPVanish παράκαμψη λογοκρισίας: Αδύναμο
Δυστυχώς, το IPVanish δεν λειτουργεί σε χώρες που υπόκεινται σε περιορισμούς. Αν ψάχνετε για ένα VPN που παρακάμπτει με συνέπεια τα τείχη προστασίας και τη λογοκρισία, τότε ίσως θα πρέπει να κοιτάξετε κάποιο από τα ExpressVPN ή Private Internet Access.
IPVanish πακέτα και τιμολόγηση
Το IPVanish προσφέρει επί πληρωμή μηνιαία και ετήσια πακέτα, τα οποία ξεκινούν από τα 2,19 $ / το μήνα. Το ετήσιο πακέτο περιλαμβάνει μία δωρεάν συνδρομή για το VIPRE Αntivirus (διαθέσιμο μόνο για Windows και macOS).
Το IPVanish δέχεται πληρωμές μέσω πιστωτικών και χρεωστικών καρτών αλλά και PayPal (δεν υποστηρίζει πληρωμές με κρυπτονομίσματα). Στο ετήσιο πακέτο λαμβάνετε εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών.
Διαβάστε την πλήρη αξιολόγηση του IPVanish >
Σύντομη σύγκριση των καλύτερων VPN του 2024
ΔΟΚΙΜΑΣΤΕ ΤΟ EXPRESSVPN (30 ΗΜΕΡΕΣ ΧΩΡΙΣ ΚΑΝΕΝΑ ΡΙΣΚΟ)
Επισήμανση συντακτών: Τα Intego, Private Internet Access, CyberGhost και ExpressVPN βρίσκονται υπό την ιδιοκτησία της Kape Technologies, της μητρικής μας εταιρείας.
Πώς να επιλέξετε το καλύτερο VPN το 2024
Για να επιλέξετε το κατάλληλο VPN, πρέπει να κάνετε τα εξής:
- Βεβαιωθείτε ότι το VPN διαθέτει προηγμένα χαρακτηριστικά ασφαλείας. Συνιστώ αποκλειστικά VPN που πληρούν τα πρότυπα ασφαλείας του κλάδου, διαθέτοντας χαρακτηριστικά όπως είναι η κρυπτογράφηση AES 256-bit, τα ασφαλή πρωτόκολλα VPN (όπως OpenVPN και WireGuard) και ο διακόπτης έκτακτης ανάγκης (που εμποδίζει την έκθεση των δεδομένων σας στο διαδίκτυο σε περίπτωση διακοπής της σύνδεσης VPN). Επίσης, αναζητώ πρόσθετες λειτουργίες, όπως ο διαχωρισμός σήραγγας (που επιτρέπει τη δρομολόγηση ενός μέρους της διαδικτυακής σας κίνησης μέσω VPN και ενός άλλου μέρους της μέσω των τοπικών σας συνδέσεων), ένα πρόγραμμα αποκλεισμού διαφημίσεων και πολλά ακόμη. Αξίζει να επισημανθεί πως δεν διαθέτουν όλα τα VPN της λίστας το σύνολο των παραπάνω πρόσθετων, ωστόσο, όλες οι κορυφαίες επιλογές μου, όπως είναι το ExpressVPN, το Private Internet Access και το CyberGhost VPN φέρουν ισχυρά χαρακτηριστικά ασφαλείας.
- Ελέγξτε την πολιτική μη καταγραφής του παρόχου. Για να αποτραπεί η αποθήκευση των προσωπικών σας πληροφοριών καθώς και των διαδικτυακών σας δραστηριοτήτων από πλευράς VPN, αυτό θα πρέπει να διαθέτει μια αυστηρή πολιτική όπου θα αναφέρεται ρητά η μη καταγραφή των δεδομένων σας — όλα τα VPN της λίστας διαθέτουν αυστηρές πολιτικές μη καταγραφής. Μάλιστα, ορισμένα VPN (όπως τα ExpressVPN, Private Internet Access, CyberGhost VPN και NordVPN) έχουν ελεγχθεί και επιβεβαιωθεί από ανεξάρτητους φορείς ή έχουν αποδειχθεί αληθή μέσω δικαστικών εγγράφων.
- Επιλέξτε έναν πάροχο VPN με μεγάλη γκάμα διακομιστών παγκοσμίως. Τα καλύτερα VPN διαθέτουν εκατοντάδες ή χιλιάδες διακομιστές ανά τον κόσμο. Περισσότεροι διακομιστές σε μια τοποθεσία συνήθως μεταφράζονται σε ταχύτερες συνδέσεις στο διαδίκτυο και μειώνουν τον κίνδυνο υπερφόρτωσης σε έναν συγκεκριμένο διακομιστή, κάτι που οδηγεί σε υψηλότερες ταχύτητες.
- Βεβαιωθείτε ότι το VPN προσφέρει γρήγορες ταχύτητες. Κάθε VPN αναμένεται να επιβραδύνει τη σύνδεσή σας στο διαδίκτυο, ωστόσο, τα καλύτερα VPN θα ελαχιστοποιήσουν αυτή τη μείωση της ταχύτητας, ακόμη και όταν θα συνδεθείτε σε απομακρυσμένους διακομιστές. Τα VPN σε αυτήν τη λίστα δεν μείωσαν την ταχύτητά μου περισσότερο από 50% — τα ταχύτερα VPN (όπως το ExpressVPN και το Private Internet Access) επιβράδυναν τη σύνδεσή μου κατά μέσο όρο μόνο 15-25%, τιμή πραγματικά καλή. Στην πραγματικότητα, ακόμη και σε περιπτώσεις όπου οι ταχύτητές μου μειώθηκαν σημαντικά, κατάφερα να περιηγηθώ στο διαδίκτυο, να μεταδώσω βίντεο και να κατεβάσω αρχεία έχοντας γρήγορη και σταθερή σύνδεση στο διαδίκτυο με κάθε VPN της λίστας.
- Προσδιορίστε τις δυνατότητες του VPN σε ό,τι αφορά το streaming, το torrenting καθώς και τη δυνατότητα λειτουργίας του σε περιοχές με λογοκρισία. Ένα καλό VPN λειτουργεί με τις διαθέσιμες κορυφαίες υπηρεσίες streaming της τοποθεσίας σας, σας επιτρέπει να μοιράζεστε με ασφάλεια αρχεία P2P, ενώ λειτουργεί σε χώρες που περιορίζουν το περιεχόμενο του διαδικτύου. Δεν είναι όλα τα VPN καλά για όλες τις διαδικτυακές δραστηριότητες, ωστόσο, πολλά από τα κορυφαία VPN μου (όπως το ExpressVPN, το Private Internet Access και το PrivateVPN) είναι καλά για streaming και torrenting, ενώ λειτουργούν σε περιοχές με διαδικτυακούς περιορισμούς και τείχη προστασίας.
- Επιλέξτε έναν πάροχο που συμφέρει συνολικά. Όλες οι επιλογές μου επιτρέπουν την ταυτόχρονη σύνδεση 5-10 συσκευών μέσω ενός λογαριασμού — μάλιστα, ορισμένες από αυτές (όπως τα Private Internet Access, Surfshark και TunnelBear) προσφέρουν απεριόριστες ταυτόχρονες συνδέσεις. Τα περισσότερα VPN διαθέτουν μηνιαία και ετήσια πακέτα συνδρομής, ευέλικτες επιλογές πληρωμής (μεταξύ των οποίων και τα κρυπτονομίσματα) και εγγυήσεις επιστροφής χρημάτων διάρκειας 30 ημερών (το CyberGhost διαθέτει εγγύηση επιστροφής χρημάτων διάρκειας 45 ημερών).
ΔΟΚΙΜΑΣΤΕ ΤΟ EXPRESSVPN (30 ΧΩΡΙΣ ΚΑΝΕΝΑ ΡΙΣΚΟ)
Πώς να επιλέξετε το καλύτερο VPN για το λειτουργικό σας σύστημα
Κατά την επιλογής ενός VPN, είναι σημαντικό να λάβετε υπόψη την ποιότητα των εφαρμογών του για τις συσκευές σας. Αν και όλα τα VPN της λίστας προσφέρουν ασφαλείς και φιλικές προς τον χρήστη εφαρμογές για τα κορυφαία λειτουργικά συστήματα, ορισμένα διαπρέπουν σε συγκεκριμένες πλατφόρμες. Για παράδειγμα, ένα VPN μπορεί να διαθέτει μια εξαιρετική Windows εφαρμογή, αλλά να στερείται σημαντικών λειτουργιών στο iOS. Επομένως, θα πρέπει να βεβαιωθείτε ότι το VPN που επιλέγετε φέρει ισχυρή υποστήριξη εφαρμογών για κάθε συσκευή που σκοπεύετε να χρησιμοποιήσετε.
Δοκίμασα τις Android, iOS, Windows και Mac εφαρμογές για κάθε VPN σε αυτήν τη λίστα. Παρακάτω αναφέρονται οι παράγοντες που θα πρέπει να λάβετε υπόψη για την επιλογή του καλύτερου VPN σε κάθε λειτουργικό σύστημα:
- Καλύτερο VPN για Windows. Η Windows εφαρμογή ενός VPN είναι συνήθως η πλουσιότερη από πλευράς λειτουργιών αλλά και η φιλικότερη προς τον χρήστη εφαρμογή του εκάστοτε παρόχου. Οι Windows συσκευές είναι συμβατές με πολλά εργαλεία VPN, επομένως θα πρέπει να βεβαιωθείτε ότι το VPN σας διαθέτει τα απαραίτητα, δηλαδή μια εύληπτη διεπαφή, έναν διακόπτη έκτακτης ανάγκης, γρήγορα και ασφαλή πρωτόκολλα καθώς και διαχωρισμό σήραγγας. Η κορυφαία μας επιλογή για τα Windows είναι το ExpressVPN.
- Καλύτερο VPN για Mac. Οι Mac εφαρμογές συνήθως διαθέτουν αρκετές ίδιες λειτουργίες VPN με τις αντίστοιχες εφαρμογές για Windows, ωστόσο υπάρχουν ορισμένες διαφορές. Για παράδειγμα, πολλές εφαρμογές VPN για Mac δεν διαθέτουν τα ταχύτερα πρωτόκολλα, προστασία διαρροών IP και διαχωρισμό σήραγγας. Οι αγαπημένες μου Mac εφαρμογές είναι αυτές των ExpressVPN και Private Internet Access.
- Καλύτερο VPN για Android. Υπάρχουν πολλές εφαρμογές VPN για Android που απλά δεν λειτουργούν, δεν διαθέτουν αρκετές λειτουργίες ή έχουν πολύπλοκο σχεδιασμό — καθιστώντας έτσι δύσκολη τη χρήση του VPN σας εν κινήσει. Ευτυχώς, τα κορυφαία VPN, όπως το ExpressVPN και το Private Internet Access, διαθέτουν Android εφαρμογές, οι οποίες είναι εξαιρετικά εύκολες στην πλοήγηση και δεν φέρουν σφάλματα.
- Καλύτερο VPN για iOS. Είναι σύνηθες οι εφαρμογές VPN για iOS να προσφέρουν τις λιγότερες δυνατότητες-λειτουργίες σε σύγκριση με τα υπόλοιπα κορυφαία λειτουργικά συστήματα, εξαιτίας των περιορισμών που θέτει η Apple στις κινητές συσκευές της. Ωστόσο, υπάρχουν[1] ορισμένες πολύ καλές εφαρμογές VPN για iOS, οι οποίες διαθέτουν σπάνιες-για iOS-λειτουργίες, όπως είναι ο διακόπτης έκτακτης ανάγκης και το πρόγραμμα αποκλεισμού κακόβουλου λογισμικού. Έχουμε αξιολογήσει τα ExpressVPN και CyberGhost VPN ως τις Νο#1 και Νο#2 εφαρμογές μας για iOS.
ΔΟΚΙΜΑΣΤΕ ΤΟ EXPRESSVPN (30 ΗΜΕΡΕΣ ΧΩΡΙΣ ΚΑΝΕΝΑ ΡΙΣΚΟ)
Σε τι βοηθά η χρήση του VPN μου;
- Βελτιωμένη ασφάλεια. Τα VPN κρυπτογραφούν τα δεδομένα σας και τα προστατεύουν από τους χάκερ, ιδίως όταν χρησιμοποιείτε δημόσια δίκτυα Wi-Fi.
- Καλύτερο απόρρητο. Τα VPN αποκρύπτουν τη διεύθυνση IP σας πίσω από τη διεύθυνση IP του διακομιστή τους, παρεμποδίζοντας έτσι τους ιστότοπους και λοιπούς τρίτους από το να δουν τη φυσική γεωγραφική τοποθεσία σας. Επίσης, τα καλά VPN διαθέτουν αυστηρές πολιτικές μη τήρησης αρχείων καταγραφής, που σημαίνει ότι αυτά δεν παρακολουθούν ούτε καταγράφουν πληροφορίες σχετικά με τις διαδικτυακές σας δραστηριότητες.
- Παράκαμψη λογοκρισίας. Τα VPN μπορούν να σας βοηθήσουν να αποκτήσετε πρόσβαση σε αποκλεισμένους ιστότοπους ή να παρακάμψετε τη διαδικτυακή λογοκρισία που επιβάλλουν ορισμένες κυβερνήσεις, δίνοντάς σας τη δυνατότητα να περιηγηθείτε ελεύθερα στο διαδίκτυο και να αποκτήσετε πρόσβαση σε πληροφορίες.
- Streaming. Ένα VPN σας επιτρέπει να παρακολουθήσετε με ασφάλεια τις αγαπημένες σας εκπομπές στις τοπικές σας βιβλιοθήκες, προστατεύοντας παράλληλα το απόρρητό σας.
- Torrenting. Τα VPN προστατεύουν την ταυτότητά σας κατά τη λήψη ή τη μεταφόρτωση torrent. Αποκρύπτουν τη διεύθυνση IP σας και κρυπτογραφούν τη διαδικτυακή σας κίνηση, διασφαλίζοντας ότι οι διαδικτυακές σας δραστηριότητες παραμένουν απόρρητες και ασφαλείς.
- Gaming. Τα VPN μπορούν να βοηθήσουν στη μείωση του κινδύνου αντιμετώπισης κατανεμημένων επιθέσεων άρνησης υπηρεσιών (DDoS), από τη στιγμή που η πραγματική σας διεύθυνση IP είναι κρυμμένη και οι επιτιθέμενοι δεν μπορούν να σας στοχεύσουν απευθείας. Επίσης, τα VPN ενδέχεται να σας προσφέρουν πρόσβαση σε παιχνίδια ή διακομιστές παιχνιδιών που φέρουν γεωγραφικούς περιορισμούς.
- Αποτροπή περιορισμού εύρους ζώνης. Τα VPN κρυπτογραφούν τη διαδικτυακή σας κίνηση, έτσι ο πάροχος υπηρεσιών διαδικτύου (ISP) σας δεν μπορεί να δει τι κάνετε στο διαδίκτυο. Χωρίς τις εν λόγω πληροφορίες, ο πάροχος δεν θα είναι σε θέση να περιορίσει ποτέ ξανά το εύρος ζώνης σας ακόμη κι αν εσείς χρησιμοποιείτε ιστότοπους streaming ή παίζετε διαδικτυακά παιχνίδια για ώρες.
ΔΟΚΙΜΑΣΤΕ ΤΟ EXPRESSVPN (30 ΗΜΕΡΕΣ ΧΩΡΙΣ ΚΑΝΕΝΑ ΡΙΣΚΟ)
Κορυφαίες εταιρείες που δεν τα κατάφεραν:
- Hotspot Shield. Το Hotspot Shield είναι ένα καλό VPN για streaming και torrenting, με γρήγορες ταχύτητες και μεγάλο δίκτυο διακομιστών. Ωστόσο, στερείται ορισμένων βασικών χαρακτηριστικών ασφαλείας, όπως είναι το γεγονός της λειτουργίας της προστασίας διαρροών IPv6 και WebRTC αποκλειστικά και μόνο στα Windows. Επίσης, δεν αποτελεί αξιόπιστη επιλογή σε ό,τι αφορά την παράκαμψη των τειχών προστασίας σε χώρες που φέρουν περιορισμούς, όπως είναι η Κίνα. Γενικότερα, δεν αξίζει τόσο όσο τα υπόλοιπα VPN σε αυτήν τη λίστα.
- HMA VPN. Το HMA VPN είναι ασφαλές, διαθέτει καλές ταχύτητες, υποστηρίζει το torrenting σε αποκλειστικούς διακομιστές P2P και λειτουργεί με δημοφιλείς ιστότοπους streaming. Ωστόσο, το HMA VPN δεν λειτουργεί σε χώρες που υπόκεινται σε περιορισμούς ως προς τη χρήση του διαδικτύου, η υποστήριξη πελατών του δεν είναι καλή, ενώ είναι και αρκετά ακριβό.
- Mullvad VPN. Το Mullvad VPN διαθέτει εντυπωσιακές λειτουργίες ασφαλείας και απορρήτου, διατηρεί αρκετά γρήγορες ταχύτητες και λειτουργεί σε χώρες με περιορισμούς στο διαδίκτυο. Παρ’ όλα αυτά, ένα από τα μεγαλύτερα μειονεκτήματα του Mullvad VPN είναι ότι δεν λειτουργεί με πολλές υπηρεσίες streaming.
Συγκριτικά γραφήματα VPN
Αν και υπάρχουν πολλά που πρέπει να λάβετε υπόψη κατά την επιλογή ενός VPN, τα παρακάτω γραφήματα με χρωματική κωδικοποίηση σας παρουσιάζουν τα χαρακτηριστικά κάθε παρόχου VPN, το απόρρητο, τις τιμές, την υποστήριξη πελατών και πολλά άλλα.
Κάθε στήλη των παρακάτω γραφημάτων αντιπροσωπεύει ένα σημαντικό κομμάτι κάθε προϊόντος ενώ υπάρχει ένα απλοποιημένο σύστημα χρωματικής κωδικοποίησης που παρουσιάζει την απόδοση των VPN σε καθεμία από τις κατηγορίες δοκιμών.
Τι μας παρουσιάζει αυτή η πληροφορία;
- Ουσιαστικά τα πάντα. Απόρρητο, ασφάλεια, ταχύτητες λήψης και μεταφόρτωσης, τιμολόγηση, υποστήριξη πελατών, χρηστικότητα ιστότοπου, κοινή χρήση δεδομένων με κυβερνήσεις και συνεργασίες, τεχνικές προδιαγραφές και πολλά άλλα.
Υπάρχουν δύο γραφήματα — ένα απλό γράφημα σύγκρισης VPN και ένα λεπτομερές γράφημα σύγκρισης VPN.
Το απλό γράφημα είναι εξαιρετικό για μη τεχνικούς χρήστες που θέλουν να ρίξουν μία γρήγορη ματιά στο τι είναι καλό, κακό και άσχημο. Ωστόσο, το λεπτομερές γράφημα παρέχει μια πιο εις βάθος εικόνα για κάθε πάροχο υπηρεσιών VPN.
Πώς να χρησιμοποιήσετε τα γραφήματα σύγκρισης VPN:
- Χρησιμοποιήστε το σύστημα χρωματικής κωδικοποίησης. Το σύστημα με χρωματική κωδικοποίηση χρησιμοποιείται και για τους δύο πίνακες και σας βοηθά να αποκτήσετε μια γρήγορη εικόνα για κάθε πτυχή ενός παρόχου VPN. Το απλοποιημένο γράφημα περιλαμβάνει ένα σύστημα 3 χρωμάτων — κόκκινο (σημαντικά ζητήματα), κίτρινο (ορισμένα ζητήματα) και πράσινο (καλό). Το λεπτομερές γράφημα προσθέτει δύο επιπλέον χρώματα — πορτοκαλί (δεν είναι καλό) και λαχανί (είναι εντάξει) — δημιουργώντας έτσι ένα σύστημα 5 χρωμάτων. Για τους χρήστες με αχρωματοψία, απλά τσεκάρετε την επιλογή «▣ Έκδοση για άτομα με αχρωματοψία».
- Χρησιμοποιήστε φίλτρα. Κάνοντας κλικ στην επιλογή «Φίλτρο» κάτω από τη λίστα παρόχων VPN, μπορείτε να επιλέξετε μια συγκεκριμένη επωνυμία που θα θέλατε να αξιολογήσετε. Κάνοντας κλικ στην επιλογή «Φίλτρο» κάτω από κάθε στήλη, μπορείτε να αναδιατάξετε τον πίνακα για να εμφανίσετε τα καλύτερα/χειρότερα VPN για μια συγκεκριμένη λειτουργία.
- Επιλέξτε τον αριθμό των καταχωρίσεων. Μεταβείτε στην επιλογή «Εμφάνιση # ▾ καταχωρίσεων» στην επάνω αριστερή γωνία κάθε γραφήματος, κάντε κλικ στο κάτω βέλος «▾» και επιλέξτε τον αριθμό των καταχωρίσεων που θέλετε να δείτε.
- Δείτε τη λίστα επεξηγήσεων όρων. Κάτω από τα απλά αλλά και τα λεπτομερή γραφήματα σύγκρισης VPN υπάρχει μια λίστα επεξηγήσεων που επεξηγεί τη σημασία κάθε όρου στο γράφημα.
- Οριζόντια κύλιση. Χρησιμοποιήστε την οριζόντια κύλιση για να δείτε κάθε στήλη στο γράφημα. Η οριζόντια κύλιση είναι απαραίτητη για να δείτε κάθε στήλη στο λεπτομερές γράφημα σύγκρισης VPN.
Απλό γράφημα σύγκρισης VPN

Το παρακάτω γράφημα παρέχει μια σύντομη επισκόπηση κάθε επωνυμίας VPN. Το γράφημα παρουσιάζει πληροφορίες όπως η δικαιοδοσία κάθε εταιρείας VPN, οι πολιτικές καταγραφής, οι τιμολογήσεις και πολλά ακόμη.
Δείτε τα επεξηγηματικά γραφήματα για μια λίστα με ορισμούς όρων καθώς και τον λόγο για τον οποίο θεωρούνται σημαντικοί.
Αναλυτικό γράφημα σύγκρισης VPN

Επεξήγηση γραφημάτων
Επεξήγηση γραφημάτων
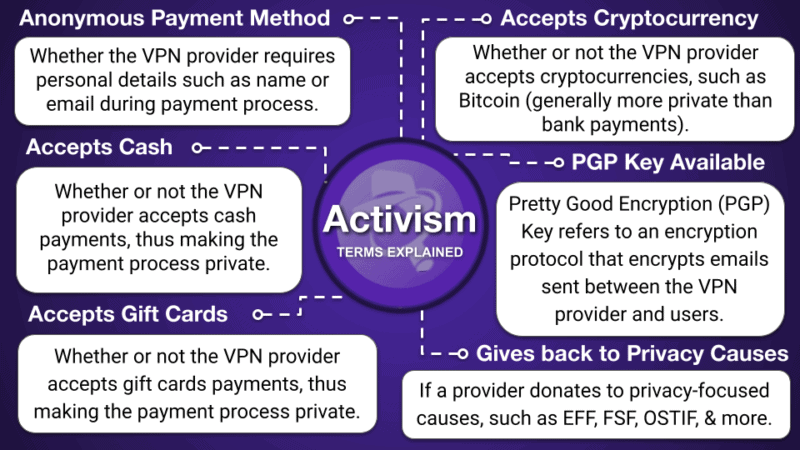
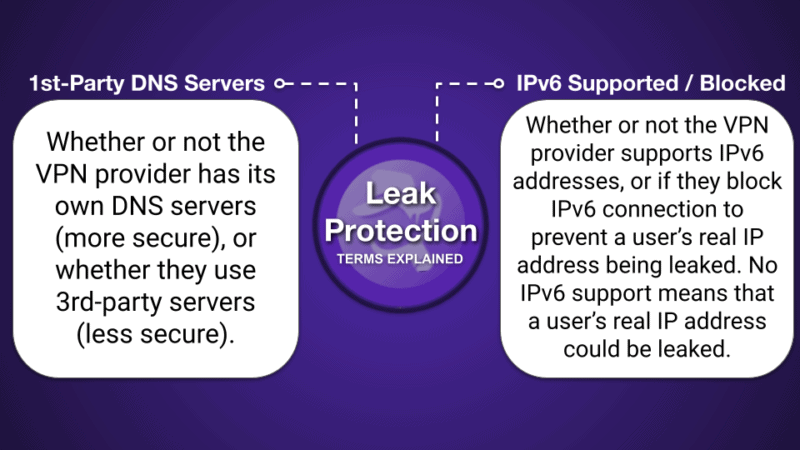
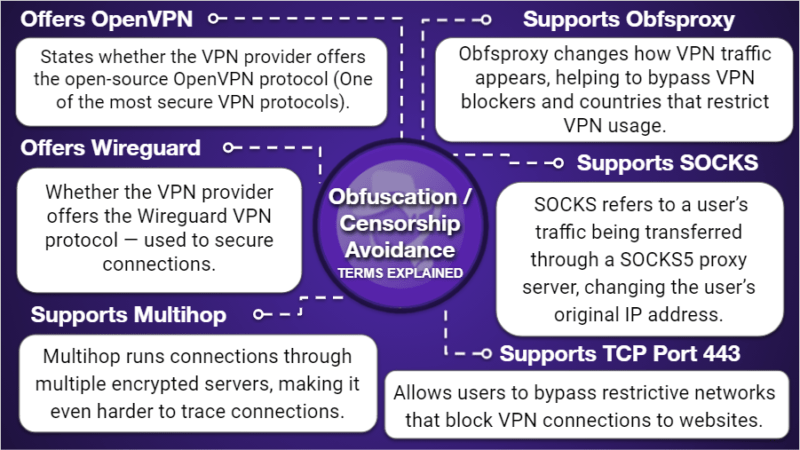
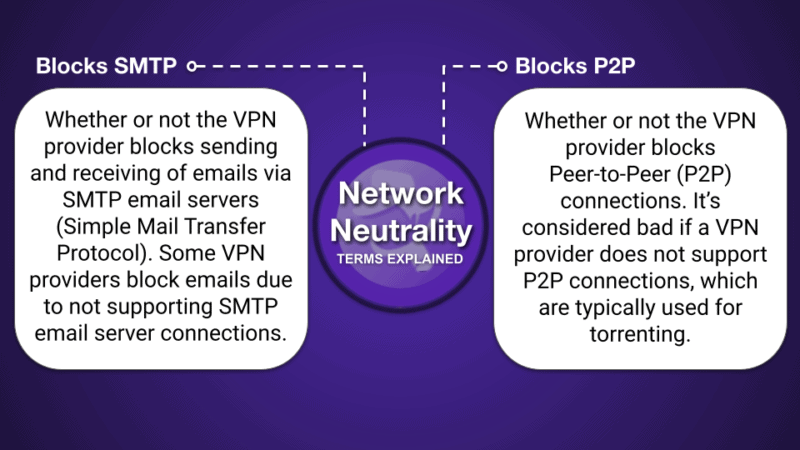
Συχνές ερωτήσεις
Ποιοι είναι το καλύτερο VPN το 2024;
To ExpressVPN είναι η Νο#1 επιλογή μου για το καλύτερο VPN το 2024. Διαθέτει μεγάλο δίκτυο γρήγορων διακομιστών, είναι πολύ εύκολο στη χρήση και φέρει εξαιρετικά χαρακτηριστικά ασφαλείας (ιδιόκτητη υπηρεσία κρυπτογράφησης DNS, τεχνολογία TrustedServer και το εξαιρετικά γρήγορο, ασφαλές ιδιόκτητο πρωτόκολλο «Lightway»). Επίσης, διατηρεί το απόρρητο των χρηστών του μέσω μιας αυστηρής πολιτικής μη καταγραφής, επιτρέπει στους χρήστες την πληρωμή μέσω κρυπτονομισμάτων, ενώ όλοι οι διακομιστές του είναι τεχνολογίας RAM (δεν διαθέτουν σκληρούς δίσκους), ώστε η μνήμη να διαγράφεται συχνά. Σας επιτρέπει να κάνετε streaming σε HD ποιότητα σε κάθε κορυφαίο ιστότοπο streaming, υποστηρίζει διαδικτυακή κίνηση P2P σε όλους τους διακομιστές του και παρακάμπτει με επιτυχία τα τείχη προστασίας σε χώρες με περιορισμούς. Μπορείτε να συνδέσετε έως και 8 συσκευές ταυτόχρονα, με το ExpressVPN να καλύπτεται από εγγύηση επιστροφής χρημάτων διάρκειας 30 ημερών. Σε κάθε περίπτωση, το καλύτερο VPN είναι αυτό που φαντάζει ιδανικό στις ανάγκες σας.
Είναι νόμιμα τα VPN;
Τα VPN είναι νόμιμα στις περισσότερες χώρες του κόσμου. Ωστόσο, ορισμένες χώρες έχουν απαγορεύσει τα VPN ή δεν επιτρέπουν τη χρήση των VPN για πρόσβαση σε λογοκριμένο περιεχόμενο. Παραδείγματα τέτοιων χωρών αποτελούν η Κίνα, το Ιράν, η Ρωσία, το Ιράκ, η Λευκορωσία, η Βόρεια Κορέα, τα Ηνωμένα Αραβικά Εμιράτα και η Βενεζουέλα. Εάν χρησιμοποιείτε ένα VPN σε μια χώρα που δεν επιτρέπεται η χρήση τους, τότε μπορεί να παραβιάζετε τη νομοθεσία. Στην προκειμένη περίπτωση, αν σας εντοπίσουν ενδέχεται να σας ασκηθεί δίωξη.
Σε περίπτωση που σκοπεύετε να ζήσετε ή να επισκεφθείτε μια χώρα που περιορίζει το περιεχόμενο των χρηστών, θα πρέπει να αγοράσετε πρότερα ένα VPN, αφού ενδέχεται να μην μπορείτε να αποκτήσετε πρόσβαση στον ιστότοπο του VPN από το εσωτερικό της εν λόγω χώρας. Το ExpressVPN αντιμετωπίζει με ιδιαίτερη επιτυχία τα τείχη προστασίας και τους διαδικτυακούς περιορισμούς.
Σε χώρες όπου τα VPN είναι νόμιμα, θεωρείται παράνομη η χρήση τους για εγκληματικές δραστηριότητες. Εφόσον ακολουθείτε όλους τους τοπικούς νόμους, ένα VPN αποτελεί ένα απολύτως ασφαλές και νόμιμο εργαλείο, το οποίο προσφέρει επιπλέον ασφάλεια, απόρρητο και ευελιξία στην διαδικτυακή σας εμπειρία.
Πώς ένα VPN σε προστατεύει στο διαδίκτυο;
Ένα VPN σας προστατεύει κυρίως με δύο τρόπους. Ο πιο βασικός τρόπος είναι με τη δρομολόγηση της διαδικτυακής σας κίνησης μέσω ενός εκ των διακομιστών του — αντί μέσω του τοπικού σας δικτύου ή ενός δημόσιου σημείου πρόσβασης Wi-Fi — καλύπτοντας έτσι την πηγή της διαδικτυακής σας κίνησης.
Επίσης, τα VPN κρυπτογραφούν όλη τη διαδικτυακή κίνηση σε μία σήραγγα, αποκρύπτοντας όλο το περιεχόμενο της περιήγησής σας. Τα VPN βοηθούν στην προστασία των δεδομένων περιήγησής σας από τρίτους παρατηρητές, όπως είναι οι χάκερ. Όλα τα VPN σε αυτήν τη λίστα μπορούν να πραγματοποιήσουν τα παραπάνω.
Τα VPN είναι ασφαλή;
Ναι, τα καλά VPN διαθέτουν ποικίλα χαρακτηριστικά ασφαλείας που προστατεύουν τα δεδομένα και το απόρρητό σας. Όλα τα κορυφαία VPN του 2024 διαθέτουν τα πρότυπα χαρακτηριστικά ασφαλείας VPN που ορίζει ο κλάδος, όπως κρυπτογράφηση AES 256-bit (η ίδια κρυπτογράφηση που χρησιμοποιείται από τράπεζες και στρατούς), διακόπτη έκτακτης ανάγκης (σας αποσυνδέει αυτόματα από το διαδίκτυο σε περίπτωση πτώσης της σύνδεσης VPN σας για αποφυγή τυχόν διαρροών δεδομένων), προστασία διαρροών DNS, WebRTC και IPv6, καθώς και αυστηρή πολιτική μη τήρησης αρχείων καταγραφής (απαγόρευση καταγραφής των δεδομένων περιήγησής σας από το VPN). Μάλιστα, ορισμένα VPN, όπως τα ExpressVPN και NordVPN, έχουν υποστεί ελέγχους από ανεξάρτητους φορείς για να επαληθεύσουν τις πολιτικές μη καταγραφής τους, ενώ άλλα, όπως τα Private Internet Access και CyberGhost VPN, εκδίδουν αναφορές διαφάνειας για να αποδείξουν τη μη αποθήκευση ή μεταφορά δεδομένων χρήστη.
Επίσης, τα περισσότερα ποιοτικά VPN περιλαμβάνουν προηγμένες λειτουργίες ασφαλείας, όπως διακομιστές αποκλειστικής τεχνολογίας RAM (τα δεδομένα δεν αποθηκεύονται ποτέ στον σκληρό δίσκο), μηχανισμό κρυπτογράφησης PFS (Perfect Forward Secrecy-αλλάζει το κλειδί κρυπτογράφησης για να αποτρέψει την παραβίαση μελλοντικών καθώς και προηγούμενων κλειδιών), ενώ συνοδεύονται από εντυπωσιακά πρόσθετα, όπως προγράμματα αποκλεισμού κακόβουλου λογισμικού και διαχωρισμού σήραγγας.
Πόσο κοστίζει ένα VPN;
Μια συνδρομή VPN μπορεί να σας κοστίσει, το λιγότερο, όσο ένας καφές ανά μήνα ή, το περισσότερο, όσο ένα μεσημεριανό γεύμα ανά μήνα, αναλόγως του πακέτου που θα επιλέξετε. Τα μακροπρόθεσμα πακέτα (1, 2 και 3 ετών πακέτα) συμφέρουν περισσότερο όντας πιο φθηνά, ενώ τα μηνιαία πακέτα φέρουν υψηλότερη τιμολόγηση.
Για παράδειγμα, το Private Internet Access διαθέτει ένα από τα φθηνότερα πακέτα που υπάρχουν — η τιμή του πακέτου διάρκειας 1 μηνά είναι λίγο τσουχτερή (αν και παραμένει συγκρίσιμη με άλλα κορυφαία VPN), αλλά το μακροπρόθεσμο πακέτο του είναι πολύ οικονομικό κοστίζοντας 2,03 $ / το μήνα. Οι τιμές του ExpressVPN, οι οποίες ξεκινούν από τα 5,49 $ / το μήνα, είναι λίγο υψηλότερος από τον μέσο όρο, αλλά αξίζει τα χρήματά του, ενώ το μακροπρόθεσμο πακέτο του συνήθως περιλαμβάνει επιπλέον μήνες δωρεάν χρήσης. Αν ψάχνετε για τα καλύτερα VPN χαμηλού κόστους στην αγορά, δείτε τις κορυφαίες επιλογές μας εδώ.
Αξίζει να πληρώσω για ένα VPN;
Ναι, 100%! Τα κορυφαία VPN προσφέρουν εξαιρετική ασφάλεια, απόρρητο και αξία σε λογική τιμή. Τα αγαπημένα μου VPN το 2024 είναι τα ExpressVPN και Private Internet Access, όντας εξίσου ασφαλή και γρήγορα, ενώ λειτουργούν με όλες τις κορυφαίες υπηρεσίες streaming (συμπεριλαμβανομένου του Netflix), επιτρέπουν το torrenting, διαθέτουν εύχρηστες εφαρμογές για σχεδόν κάθε συσκευή που διαθέτει σύνδεση στο διαδίκτυο και προσφέρουν ανταγωνιστικές τιμές.
Θα μπορούσατε να αποκτήσετε ένα δωρεάν VPN, αλλά πραγματικά δεν σας το συνιστώ. Τα περισσότερα δωρεάν πακέτα VPN θέτουν όρια δεδομένων ανά ημέρα ή μήνα, περιορίζουν τις ταχύτητες σας ή τον αριθμό των διακομιστών και των χωρών στις οποίες μπορείτε να αποκτήσετε πρόσβαση, ενδέχεται να διακόψουν την περιήγησή σας με διαφημίσεις ή ακόμη και να μεταπωλήσουν τα δεδομένα σας στο διαδίκτυο (τους ιστότοπους που επισκέπτεστε και τα προϊόντα που αγοράζετε) σε τρίτους για διαφημιστικούς σκοπούς.
Πώς γνωρίζω ότι το VPN μου λειτουργεί;
Μπορείτε να ελέγξετε εάν το VPN σας λειτουργεί χρησιμοποιώντας έναν ηλεκτρονικό έλεγχο διεύθυνσης IP (όπως το ipleak.net). Εάν η διεύθυνση IP που εμφανίζεται στον ιστότοπο είναι διαφορετική από την πραγματική σας τοποθεσία, τότε το VPN σας λειτουργεί σωστά. Επίσης, μπορείτε να ελέγξετε την κατάσταση του VPN από την εφαρμογή για κινητά ή υπολογιστή που διαθέτετε. Βεβαιωθείτε ότι επισημαίνεται η ένδειξη «Connected» (Συνδέθηκε).
Έλεγξα όλα τα VPN σε αυτήν τη λίστα για διαρροές. Δοκίμασα 10+ διακομιστές από κάθε πάροχο και δεν αντιμετώπισα καμία διαρροή. Επομένως, όλα λειτουργούν όπως προβλέπεται.
Πώς θα μειώσω το κόστος ενός VPN;
Για να μειώσετε το κόστος ενός VPN, θα πρέπει να εγγραφείτε σε ένα μακροπρόθεσμο πακέτο αντί σε ένα πιο σύντομο χρονικά πακέτο. Συνήθως, τα VPN προσφέρουν σημαντικές εκπτώσεις στα ετήσια πακέτα τους σε σχέση με τις μηνιαίες συνδρομές τους — για παράδειγμα, το ExpressVPN προσφέρει 3 μήνες δωρεάν χρήσης για το μεγαλύτερο σε χρονική διάρκεια πακέτο του.
Επιπλέον, έχετε κατά νου τις προωθητικές προσφορές ή τους κωδικούς κουπονιών που μπορούν να σας βοηθήσουν να εξοικονομήσετε χρήματα κατά την εγγραφή σας σε μια υπηρεσία VPN. Ο ευκολότερος τρόπος για να βρείτε τις καλύτερες προσφορές VPN είναι να προσθέτετε την εν λόγω σελίδα στους σελιδοδείκτες σας και να την ελέγχετε τακτικά.
Ένα VPN θα με κάνει ανώνυμο στο διαδίκτυο;
Τα VPN προστατεύουν το απόρρητο και τα δεδομένα σας, αλλά δεν σας καθιστούν 100% ανώνυμο. Ένα VPN κρυπτογραφεί τη διαδικτυακή σας κίνηση και αλλάζει τη διεύθυνση IP σας, δυσκολεύοντας τους άλλους να παρακολουθήσουν τις διαδικτυακές σας δραστηριότητες και την τοποθεσία σας. Ωστόσο, ένα VPN δεν μπορεί να αποτρέψει τη συλλογή όλων των δεδομένων σας από τους ιστότοπους — για παράδειγμα, δεν μπορεί να εμποδίσει τους ιστότοπους μέσων κοινωνικής δικτύωσης να συλλέξουν προσωπικά δεδομένα που δημοσιοποιείτε σε αυτούς.
Ένα VPN μπορεί να αυξήσει τις ταχύτητες;
Ορισμένες φορές, ναι. Τα VPN δεν αυξάνουν απαραίτητα τις ταχύτητες σας. Στην πραγματικότητα, τα VPN συνήθως επιβραδύνουν τις συνδέσεις σας, επειδή κρυπτογραφούν τη διαδικτυακή σας κίνηση. Η κρυπτογράφηση απαιτεί χρόνο, αφού η σύνδεσή σας πρέπει να ταξιδέψει επιπλέον για να δρομολογηθεί μέσω του διακομιστή VPN προτού φτάσει στον τελικό προορισμό της.
Ωστόσο, σε περίπτωση που ο πάροχος υπηρεσιών διαδικτύου (ISP) σας μειώσει τις ταχύτητές σας εξαιτίας των απαιτητικών-από πλευράς εύρους ζώνης-δραστηριοτήτων που πραγματοποιείτε, όπως είναι το streaming ή το gaming, η σύνδεση σε ένα VPN θα σας δώσει μία ώθηση.
Παρ’ όλα αυτά, τα κορυφαία VPN που σας προτείνω έχουν ελάχιστη επίδραση στις ταχύτητες σας. Όλα τους προσφέρουν πολύ γρήγορες ταχύτητες, έτσι, δεν θα παρατηρήσετε καν ότι είστε συνδεδεμένοι σε ένα VPN! Στις δοκιμές μου, το ExpressVPN ήταν το πιο γρήγορο.